 |
BIS611S - BUSINESS INFORMATION SYSTEMS - 1ST OPP - JUNE 2022 |
 |
1 Page 1 |
▲back to top |
nAmlBIA UnlVERSITY
OF SCIEnCE Ano TECHnOLOGY
FACULTY OF COMMERCE, HUMAN SCIENCE AND EDUCATION
DEPARTMENTOF MANAGEMENT
QUALIFICATION:BACHELOROF BUSINESSAND INFORMATION ADMINISTRATION
QUALIFICATIONCODE: BBIA
LEVEL: 6
COURSECODE: BIS611S
COURSENAME: BUSINESSINFORMATION
SYSTEMS
SESSION:JUNE 2022
DURATION: 2 HOURS
PAPER:THEORY (PAPER 1)
MARKS: 100
FIRST OPPORTUNITY EXAMINATION QUESTION PAPER
EXAMINER(S) MS S DU PLESSIS
DR N ANGULA
MODERATOR: MS D OLIVIER
INSTRUCTIONS
1. Answer ALL the questions.
2. Read all the questions carefully before answering.
3. Number the answers clearly
THIS QUESTION PAPERCONSISTSOF 8 PAGES(Including this front page)
 |
2 Page 2 |
▲back to top |
2
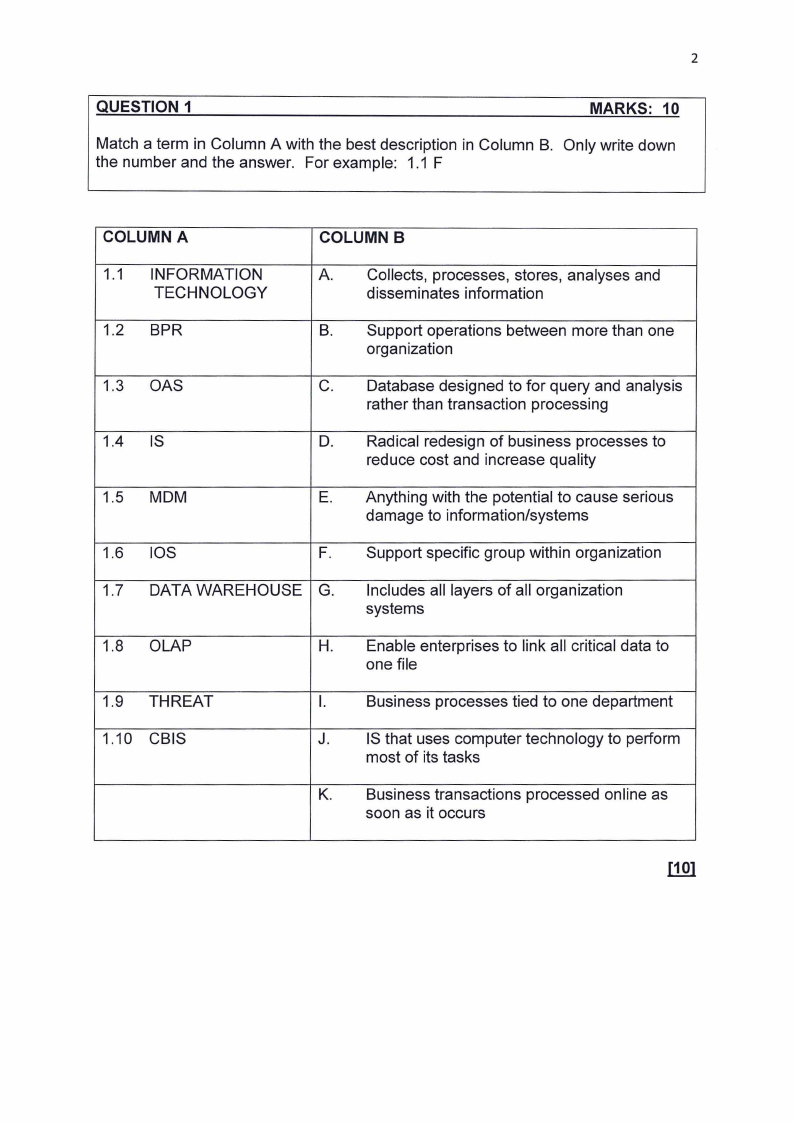
QUESTION 1
MARKS: 10
Match a term in Column A with the best description in Column B. Only write down
the number and the answer. For example: 1.1 F
COLUMN A
COLUMN B
1.1 INFORMATION
TECHNOLOGY
A. Collects, processes, stores, analyses and
disseminates information
1.2 BPR
B. Support operations between more than one
organization
1.3 OAS
C. Database designed to for query and analysis
rather than transaction processing
1.4 IS
D. Radical redesign of business processes to
reduce cost and increase quality
1.5 MOM
E. Anything with the potential to cause serious
damage to information/systems
1.6 IOS
F. Support specific group within organization
1.7 DATA WAREHOUSE G.
Includes all layers of all organization
systems
1.8 OLAP
H. Enable enterprises to link all critical data to
one file
1.9 THREAT
I.
Business processes tied to one department
1.10 CBIS
J. IS that uses computer technology to perform
most of its tasks
K. Business transactions processed online as
soon as it occurs
I1Ql
 |
3 Page 3 |
▲back to top |

3
QUESTION 2
MARKS: 10
Answer the following multiple choice questions. Only write down the question
number and the correct answer. E.g. 2.1 (c)
2.1 Identify some of the security threats we experience nowadays.
a) Spyware, lost data, pop-ups
b) Trojan horses, worms, rootkits
c) Key loggers, viruses, lock-ups
d) All of the above
2.2 What is the basis or platform of the IT infrastructure?
a) IT services
b) IT Personnel
c) IT Components
d) All of the above
2.3 Acts performed without malicious intent but provide a serious threat to
information security is called?
a) Information security
b) Privacy security
c) Unintentional threats
d) Intentional security
2.4 What governs decision-making, and code of conduct governing actions,
representing two common ways that companies self-regulate their policies?
a) Ethics
b) Code of ethics
c) The law
d) The government
2.5 What are the three most common public places that store personal
information about us, covered in the textbook?
a) Companies, warehouses and the bank
b) The bank, social media and the university
c) The university, home affairs and the internet
d) None of the above
2.6 A business continuity plan is also called a .................. .
a) Business plan
b) Disaster recovery plan
c) Economical plan
d) None of the above
 |
4 Page 4 |
▲back to top |

4
2.7 The value chain has primary and secondary activities. Please select from the
groupings which one is inclusive of primary activities.
a) Inbound logistics, operations and customer service
b) Operations and Human resource management
c) Customer service, outbound logistics and procurement
d) All of the above
2.8 What does SIS stand for?
a) System Information Stand
b) Strategic Information System
c) Support Inactivity Suffice
d) None of the above
2.9 ................................. is the tight integration of the IT function with the
organisation's strategy, mission and goals, where the IT function supports the
business objectives for the organisation.
a) Strategic plans
b) Cost leadership strategy
c) Decisions support systems
d) Business-Information technology
2.1O Which of the following are not part of the five components of an information
system.
a) hardware, software, database and people
b) hardware, systems, data and people
c) hardware, systems, information and people
d) None of the above
I1Ql
 |
5 Page 5 |
▲back to top |
5
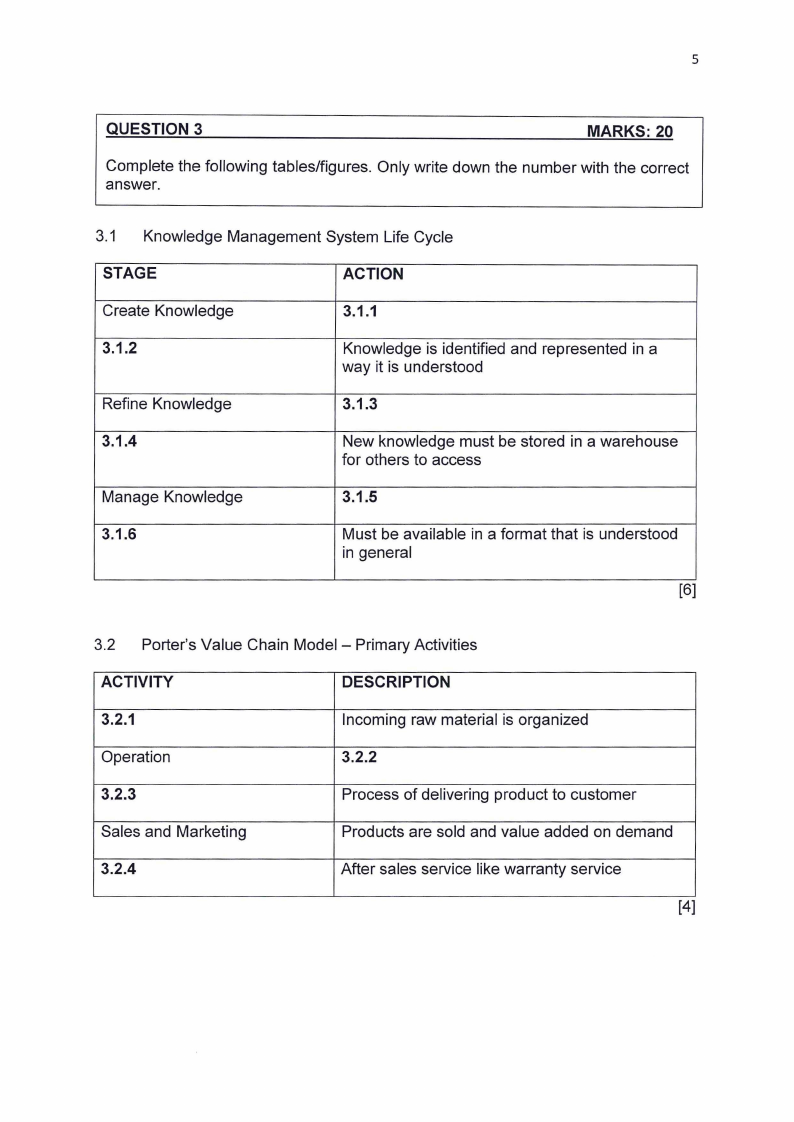
QUESTION 3
MARKS: 20
Complete the following tables/figures. Only write down the number with the correct
answer.
3.1 Knowledge Management System Life Cycle
STAGE
ACTION
Create Knowledge
3.1.1
3.1.2
Knowledge is identified and represented in a
way it is understood
Refine Knowledge
3.1.3
3.1.4
New knowledge must be stored in a warehouse
for others to access
Manage Knowledge
3.1.5
3.1.6
Must be available in a format that is understood
in general
[6]
3.2 Porter's Value Chain Model - Primary Activities
ACTIVITY
DESCRIPTION
3.2.1
Incoming raw material is organized
Operation
3.2.2
3.2.3
Process of delivering product to customer
Sales and Marketing
Products are sold and value added on demand
3.2.4
After sales service like warranty service
[4]
 |
6 Page 6 |
▲back to top |
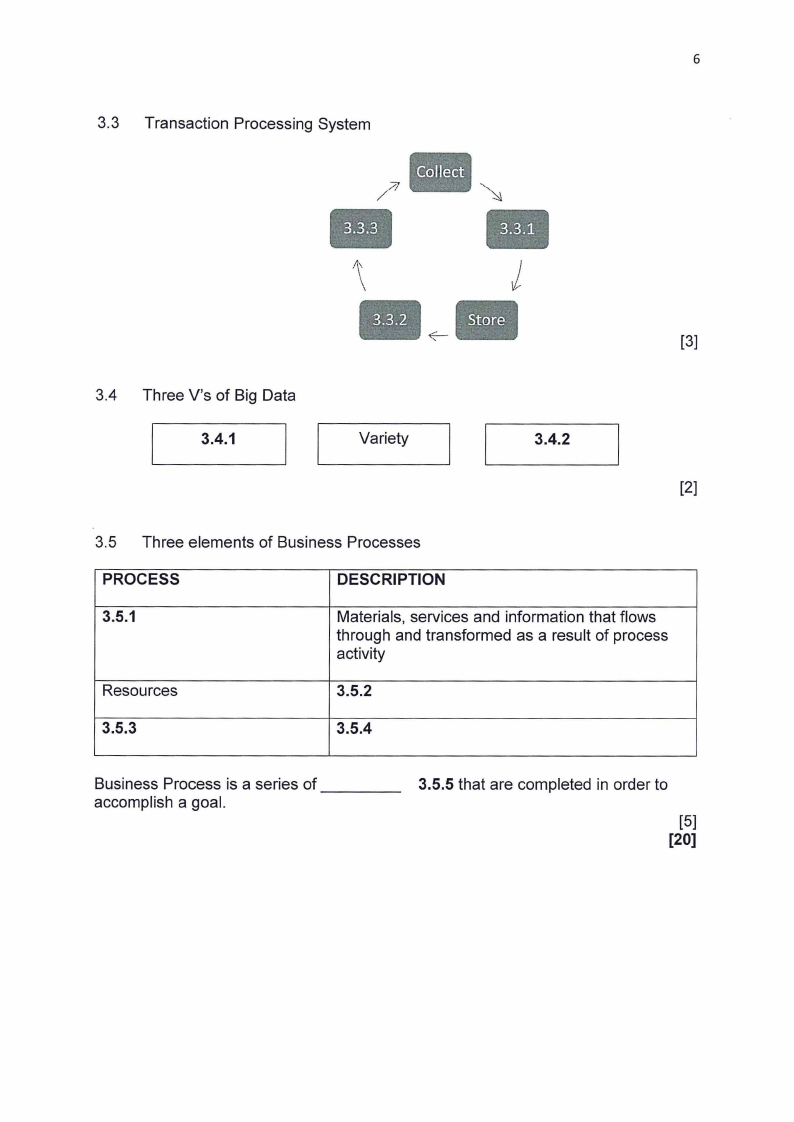
6
3.3 Transaction Processing System
[3]
3.4 Three V's of Big Data
~--3-.4-.1--~II
l ~_I_ __ v_a_r__ie_-ty
3_.4___.2
[2]
3.5 Three elements of Business Processes
PROCESS
DESCRIPTION
3.5.1
Materials, services and information that flows
through and transformed as a result of process
activity
Resources
3.5.2
3.5.3
3.5.4
Business Process is a series of ----
accomplish a goal.
3.5.5 that are completed in order to
[5]
[20]
 |
7 Page 7 |
▲back to top |
QUESTION 4
Provide clear answers to the following questions.
7
MARKS: 30
4.1 Discuss the three fundamental tenets on which ethics in general is based.
[6]
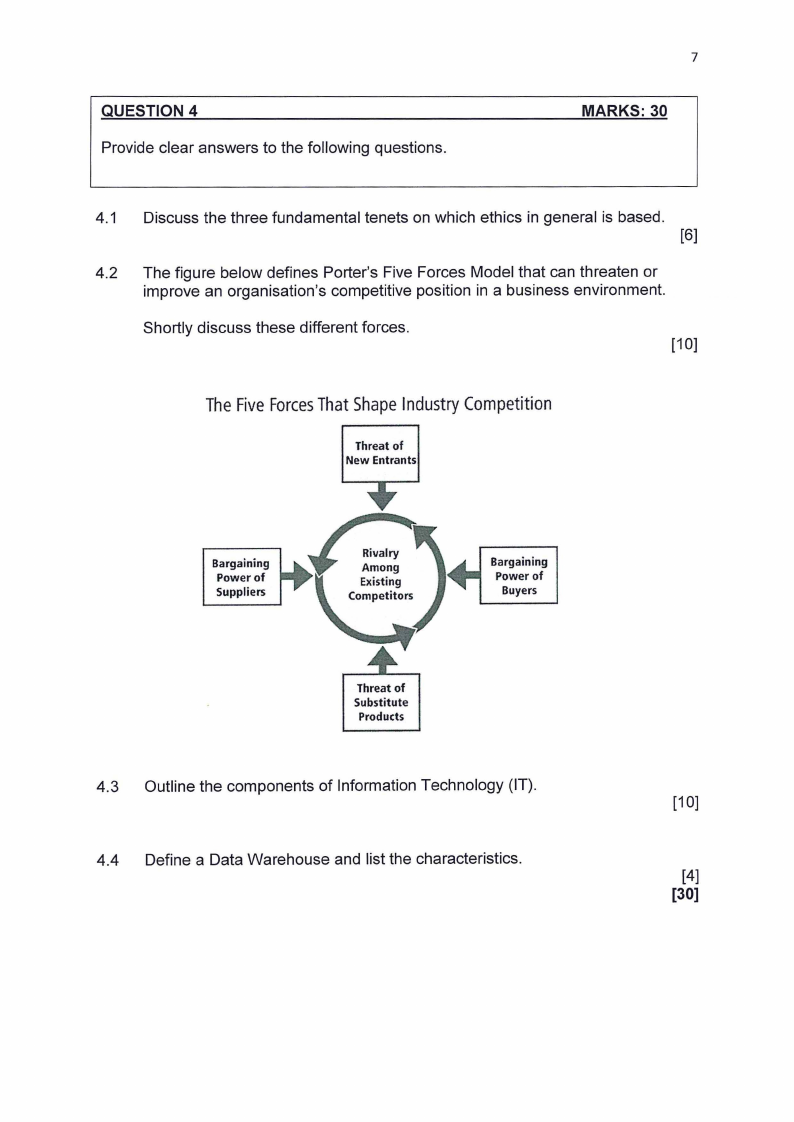
4.2 The figure below defines Porter's Five Forces Model that can threaten or
improve an organisation's competitive position in a business environment.
Shortly discuss these different forces.
[1O]
TheFiveForcesThatShapeIndustryCompetition
Threat of
New Entrants
Bargaining
Power of
Suppliers
Bargaining
••-
Powerof
Buyers
Threat of
Substitute
Products
4.3 Outline the components of Information Technology (IT).
4.4 Define a Data Warehouse and list the characteristics.
[1O]
[4]
[30]
 |
8 Page 8 |
▲back to top |

QUESTION 5
Answer the following questions correctly.
8
MARKS: 30
5.1 In order to explain Knowledge Management, clearly differentiate between tacit
knowledge and explicit knowledge.
[5]
5.2 Discuss two major categories of information security threats.
[5]
5.3 Discuss the type of Information System illustrated below.
[4]
5.4 List the areas in which Information Systems have an important impact on
organisations.
[6]
5.5 Name 6 typical challenges experienced with the managing of data.
[6]
5.6 Define Information Security and list 3 types of controls
[4]
[30]
TOTAL: 100





