 |
DTN611S - DATA NETWORKS - 1ST OPP - JUNE 2022 |
 |
1 Page 1 |
▲back to top |
n Am I BI A u n IVER s I TY
OF SCIEnCE Ano TECHnOLOGY
FACULTY OF COMPUTING AND INFORMATICS
DEPARTMENT OF COMPUTER SCIENCE
QUALIFICATION: BACHELOR OF COMPUTER SCIENCE, BACHELOR OF INFORMATICS
QUALIFICATION CODE: 07BACS, 07BAIF
LEVEL: 7
COURSE NAME: DATA NETWORKS
DATE: JUNE 2022
DURATION: 2 HOURS
COURSE CODE: DTN611S
PAPER: THEORY
MARKS: 70 (100%)
Examiners
Moderator
FIRST OPPORTUNITY EXAMINATION QUESTION PAPER
MR. NASIMANE EKANDJO, MR SHADRECK CHITAURO, MR. PETER GALLERT, AND
MS. ALBERTINA SHILONGO
PROF. GUY-ALAIN ZODI LUSILAO
THIS QUESTIONPAPERCONSISTSOF 6 PAGES(Including this front page)
INSTRUCTIONS
1) Answer ALL the questions on the answer scripts provided.
2) Be guided by the number of marks allocated when answering the questions.
3) Write clearly and neatly.
4) Show all your calculations.
5) Number your questions clearly.
1
 |
2 Page 2 |
▲back to top |

Question 1: Write down the question number and correct answer next to it. Where you are asked to
fill in, use full words, not abbreviations.
1. The path through which data travels from the sender to the receiver on the network is called:
a) Protocols
b) Standard
c) Transmission Media
d) Signals
2. Which of the following correctly defines the function for the DHCPserver on the network?
a) To assign IP address automatically to devices on the network.
b) To translate IP addresses into domain names.
c) To act as an intermediary between clients and remote servers.
d) To host websites.
3. One of the disadvantages of a Star topology is:
a) Devices are managed centrally in the topology.
b) If the central device becomes faulty, all devices will be affected.
c) It is very expensive to set up as devices are connected to each other
d) Devices are connected in a circle, if one device becomes faulty, the whole topology is
affected.
4. A MAN network could easily be described as the network that spans:
a) A country
b) A city
c) A building
d) A house
5. Which layer of the OSI model ensures that data is received in its usable format?
a) Physical
b) Presentation
c) Application
d) Data Link
6. Which port is used by FTPto transfer data?
a) Port 80
b) Port 21
c) Port 20
d) Port 25
7. The default subnet mask for IP address 128.128.45.4 is:
2
 |
3 Page 3 |
▲back to top |

a) /18
b) /17
c) /16
d) /8
8. _____________
area set of rules aimed at governing computer network
products made by different manufacturers to ensure that they can communicate.
9. The default TCP max segment size is _________
_
10. Using HTTP, the _______
method is sent to append a web page.
11. In HTTP, code _________
indicates redirection.
12. Each network interface card comes embedded with a unique address from the
a manufacturer called -----------------
13. Routers are only used in WAN.
a) True
b) False
14. Wireless transmission can be done via radio waves only.
a) True
b) False
15. A session must be terminated at the end of each packet sent.
a) True
b) False
[15 Marks]
Question 2
Maria would like to send an email to Tom. To achieve this, she must use her mail agent to compose the
e-mail. For this e-mail to reach Tom 's mailbox successfully and for Tom to access it from any of his
devices connected to the network, there are two main protocols involved.
2.1 Identify two application layer protocols that are responsible for sending and delivering the email
from Maria's mail agent to Tom's mailbox and explain their function.
(4)
2.2. For the message to reach its designated recipient, the use of a DNS server is crucial in the process.
Explain the function of the DSN Server when sending e-mails.
(2)
2.3 DNS and DHCP servers are a few examples of network servers. Write down the generic names of
the following network servers.
(3)
a) Server storing web pages:
3
 |
4 Page 4 |
▲back to top |
b) Server storing electronic mails:
c) Server storing your course materials:
2.4 Below are some of the basic commands that Network administrators use in their daily routines and
troubleshooting. Explain the purpose of each command listed below.
(4)
{a) ipconfig /all
{b) trace route
{c) nslookup
{d) ARP:
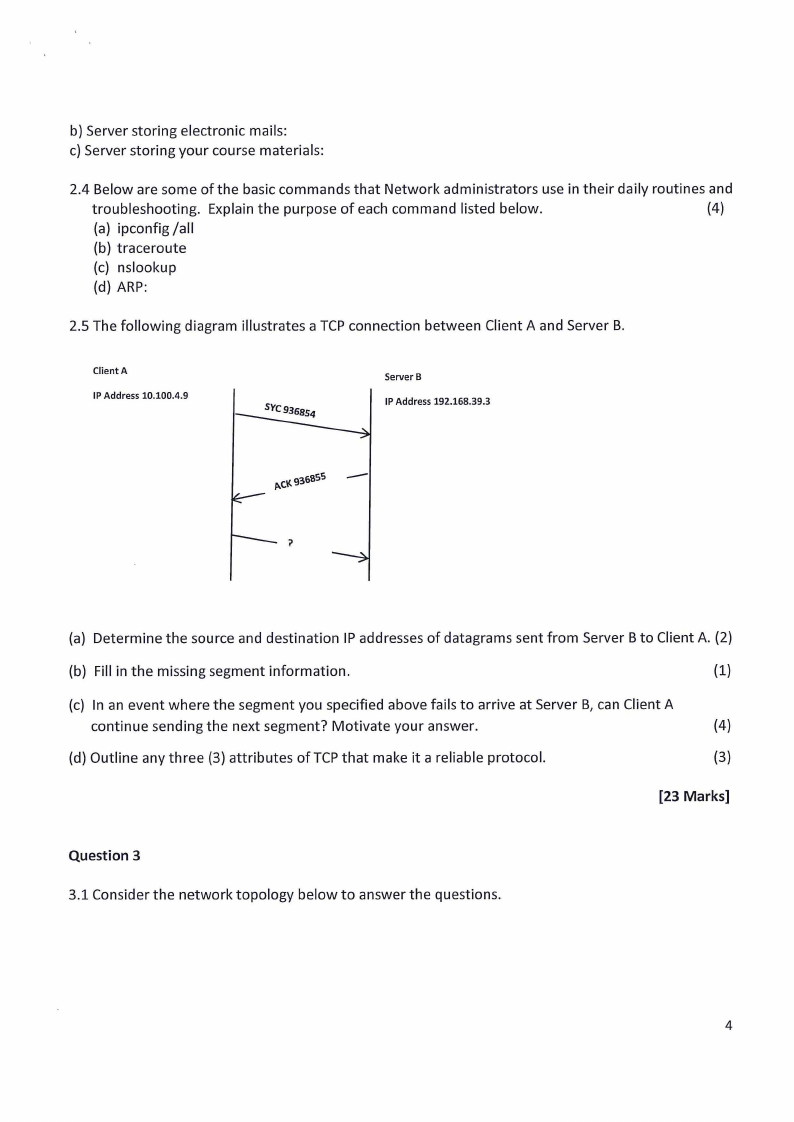
2.5 The following diagram illustrates a TCP connection between Client A and Server B.
Client A
IP Address 10.100.4.9
Server B
IP Address 192.168.39.3
-
{a) Determine the source and destination IP addresses of datagrams sent from Server B to Client A. {2)
{b) Fill in the missing segment information.
(1)
{c) In an event where the segment you specified above fails to arrive at Server B, can Client A
continue sending the next segment? Motivate your answer.
{4)
{d) Outline any three {3) attributes of TCP that make it a reliable protocol.
{3)
[23 Marks]
Question 3
3.1 Consider the network topology below to answer the questions.
4
 |
5 Page 5 |
▲back to top |
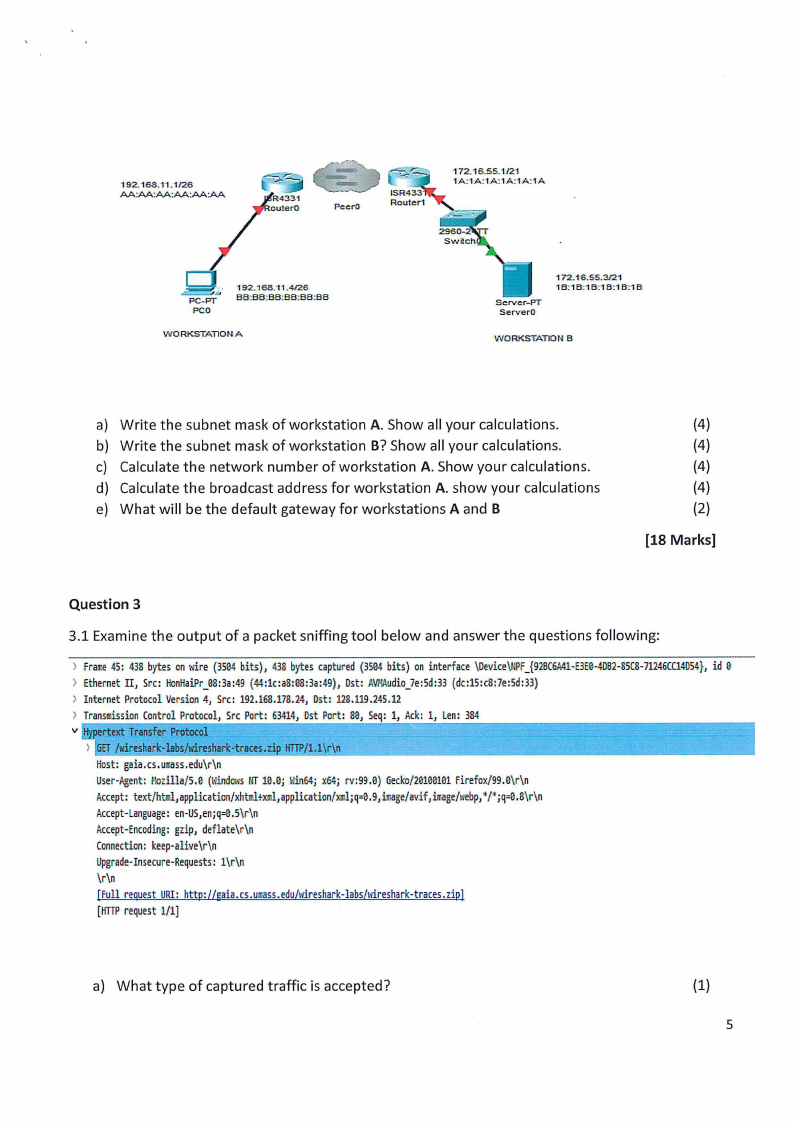
192.168.11.1/26
AA:AA:AA:AA:AA:AA
PeerD
r
;"-
PC-PT
PCO
192.168.11.4/26
BB:BB:BB:BB:BB:BB
WORKSTATION A
172.16.55.1 /21
1A:1A:1A:1A:1A:1A
Server-PT
ServerO
172.16.55.3121
1 B:1B:1 B:1 B:1 B:1 B
WORKSTATION B
a) Write the subnet mask of workstation A. Show all your calculations.
b) Write the subnet mask of workstation B?Show all your calculations.
c) Calculate the network number of workstation A. Show your calculations.
d) Calculate the broadcast address for workstation A. show your calculations
e) What will be the default gateway for workstations A and B
(4)
(4)
(4)
(4)
(2)
[18 Marks]
Question 3
3.1 Examine the output of a packet sniffing tool below and answer the questions following:
> Fra1te45: 438bytes onwire (3504bit5), 438bytes captured(3504bits) on interface \\DeviceVIPF_{92BC6A41-E3E0-40B2-85C8-71i2d460CG4D54},
> EthernetII, Src: HcnHaiPr_08:3a:(4494:lc:a8:08:3a:49),Dst: AVMAudio_7e:5(dd:c3:315:c8:7e:5d:33)
Internet ProtocolVersion4, Src: 192.168.178.24O, st: 128.119.245.12
TransmissionControlProtocol, Src Port: 63414,Dst Port: 80, Seq: 1, Ack:1, Len:384
v rtextTransfePrrotocol
GET/wiresharlc-labs/wiresharlc-ztiraIcITeTs.P/1.\\1r\\n
Host: gaia.cs.umass.edu\\r\\n
User-1\\i;enMt: ozilla/5.0(WindmN~sT10.0; Win64x; 64; rv:99.0) Gecko/201001F0i1refox/99.0\\r\\n
Accept:text/html,application/xhtm+lxmla,pplication/xml;q=90,.irnage/avfi, irnage/l~eb*/p*,; q=O8.\\r\\n
Accept-Languageen:-USe,n;q=05. \\r\\n
Accept-Encodingz: ip, deflate\\r\\n
Connectionk: eep-alive\\r\\n
UpgradeIn- secure-Requests1:\\r\\n
\\r\\n
[Full request URI:http://gaia .cs.umasse.du/wireshark-labs/wireshark-traczeisp. ]
[HTTrPequest 1/1]
a) What type of captured traffic is accepted?
(1)
5
 |
6 Page 6 |
▲back to top |

b} Is this an HTTP request of the response packet?
{1}
c} What languages (if any} does your browser indicate that it can accept?
(1)
d} Which underlying protocol was used to access this packet, justify your answer?
{2}
e} What is the MAC address of the device that requested this packet?
(1)
f} Which browser was used by the client to request this packet?
(1)
g} What is the domain name for IP address 128.119.245.12?
(1)
h} Identify and write down specific information that relates to layer 2,3 and 4 of the OSI model.
{6}
[Total marks: 70]
Paper ends
[14 Marks]
6





