 |
DTN611S - DATA NETWORKS - 1ST OPP - JUNE 2024 |
 |
1 Page 1 |
▲back to top |

nAmlBIA UnlVERSITY
·- OF SCIEnCE Ano TECHnOLOGY
Faculty of Computing and Informatics
Department of Computer Science
QUALIFICATION: BACHELOR OF COMPUTER SCIENCE
QUALIFICATION CODE: 07BCMS,
07BAIT, 07BCCY, 07BACS
COURSE: DATA NETWORKS
DATE: JUNE
DURATION: 3 HOURS
LEVEL: 6
COURSE CODE: DTN611S
PAPER: FIRST OPPORTUNITY
MARKS: 100
FIRST OPPORTUNITY EXAMINATION QUESTION PAPER
EXAMINER(S)
NDESHIHAFELA KAKWAMBI
MODERATOR:
LOIN! IIYAMBO
THIS QUESTION PAPER CONSISTS OF 7 PAGES (Excluding this front page)
INSTRUCTIONS
1. Answer ALL the questions in the answer sheets provided.
2. Write clearly and neatly.
3. Number the answers clearly.
4. When answering questions, you should be guided by the allocation of marks. Do not give
too few or too many facts in your answers.
PERMISSIBLE MATERIALS
1. Non-programmable calculator
 |
2 Page 2 |
▲back to top |

SECTION A:
[10)
Write True (T) or False (F)
Question I: The encryption of data transmitted over a network happens at layer 5 of the Open
Systems Interconnection (OSI) model.
Question 2: A device that connects to a network without the use of cables is said to be a wireless
device.
Question 3: It is not possible to configure two (2) IPv4 addresses from different subnets on a
single host.
Question 4: Sockets are physical endpoints used for communication between hosts over a
network.
Question 5: A /17 subnet can be written in clotted decimal notation as 255.255.192.0
Question 6: A Local Area Network (LAN) connects laptops, mobile phones, and appliances
within a home.
Question 7: A switch forwards bits as the unit of data in computer networks.
Question 8: The User Datagram Protocol uses pmt 53 for domain name resolutions.
Question 9: The encapsl1lation process occurs as data travels from layer 7 to layer 1 of the OSI
model.
Question 10: The Open System Interconnection (OSI) model is a conceptual model providing
a framework for network communication.
1
 |
3 Page 3 |
▲back to top |

SECTION B:
[20]
Circle the correct answer(s).
Question 1: Which device protects an internal network from external networks?
a. Firewall
b. Router
c. Vi1iual Private Network
d. Antivirus
Question 2: A web client is receiving a response from a web server. From the perspective of
the client, what is the correct order of the protocol stack that is used to decode the received
transmission?
a. Ethernet, IP, TCP, HTTP
b. HTTP, TCP, IP, Ethernet
c. Ethernet, TCP, IP, HTTP
d. HTTP, Ethernet, IP, TCP
Question 3: Which physical medium uses the propagation of light to transmit data?
a. Twisted Pair Cable
b. Coaxial Cable
c. Fibre-Optic Cable
d. Microwave
Question 4: Which of the following is not a goal of an ideal multiple-access protocol?
a. Simple
b. Fair
c. Centralised
d. Efficient
Question 5: What is the directed broadcast address of a subnet containing an IP address of
172.16.1.10 /19?
a. 172.16.1.255
b. 172.16.31.255
C. 172.16.255 .255
d. 172.16.31.254
Question 6: Which methods are used to upload and download files on webservers?
a. Src and Dest
b. PUT And GET
c. Upload and Download
d. SYN and ACK
2
 |
4 Page 4 |
▲back to top |

Question 7: Two or more nodes transmitting data at the same time on the same chmmel in a
network can cause?
a. Conflict
b. Collision
c. Corruption
d. Congestion
Question 8: How many bits are there in an JPv6 address?
a. 64 bits
b. 128 bits
c. 32 bits
d. 256 bits
Question 9: An attempt to make a computer resource unavailable to its intended users is
called?
a. Denial-of-service attack
b. Botnet attack
c. Worms attack
d. None of the above
Question 10: This is one of the network architectures used in network communication?
a. Point to Point
b. Peer to Peer
c. Token Ring
d. Server to Peer
Question 11: What is the binary equivalence of the decimal number 520?
a. 1000001001
b. 1000001000
C. 1000001010
d. 1001001000
Question 12: Which statement is correct about the function of network protocols?
a. Network protocols define the type of hardware that is used and how it is mounted.
b. They define how messages are exchanged between the source and the destination.
c. They all function at the network layer of the TCP/IP model.
d. They are only required for the exchange of messages between devices on remote
networks.
Question 13: What is latency in computer networking?
a. The amount of data that can be transmitted per unit time
b. The number of errors encountered during data transmission
c. The time it takes for data to travel from source to destination
d. The capacity of the network to handle simultaneous connections
3
 |
5 Page 5 |
▲back to top |

Question 14: What network mechanism is employed to manage the transmission of data over a
conummication channel, preventing packet loss due to excessive data transmission?
a. Congestion Control
b. Timers
c. Flow Control
d. Sliding Window
Question 15: Which of the following is a valid inet address on a network?
a. 192.60.256.0
b. 172.255.1001.0
C. 10.255.255.255
d. 255.255.255.255
Question 16: Which command can be executed to display the available network interfaces on
a computer?
a. Netstat
b. Arp -a
c. Ifconfig
d. Nslookup
Question 17: Which statement is true about the CSMA/CD access method that is used in
Ethernet?
a. When a device hears a carrier signal and transmits data, a collision cannot occur.
b. All network devices must listen before transmitting.
c. Only the devices that were involved in a collision need to execute a backoff timer.
d. Devices involved in a collision get priority to transmit after the backoff period.
Question 18: A completely interconnected network topology is called a ____
?
a. Mesh
b. Hybrid
c. Star
d. Bus
Question 19: A device that changes its access point to a network is said to be?
a. Stationary
b. Wireless
c. Temporary
d. Mobile
Question 20: Under which circumstances will a switch flood a frame out of every port except
the port that the frame was received on?
a. The broadcast address is the destination address.
b. The source address is the destination address.
c. The source address is multicast.
d. The destination address is a known unicast address.
4
 |
6 Page 6 |
▲back to top |
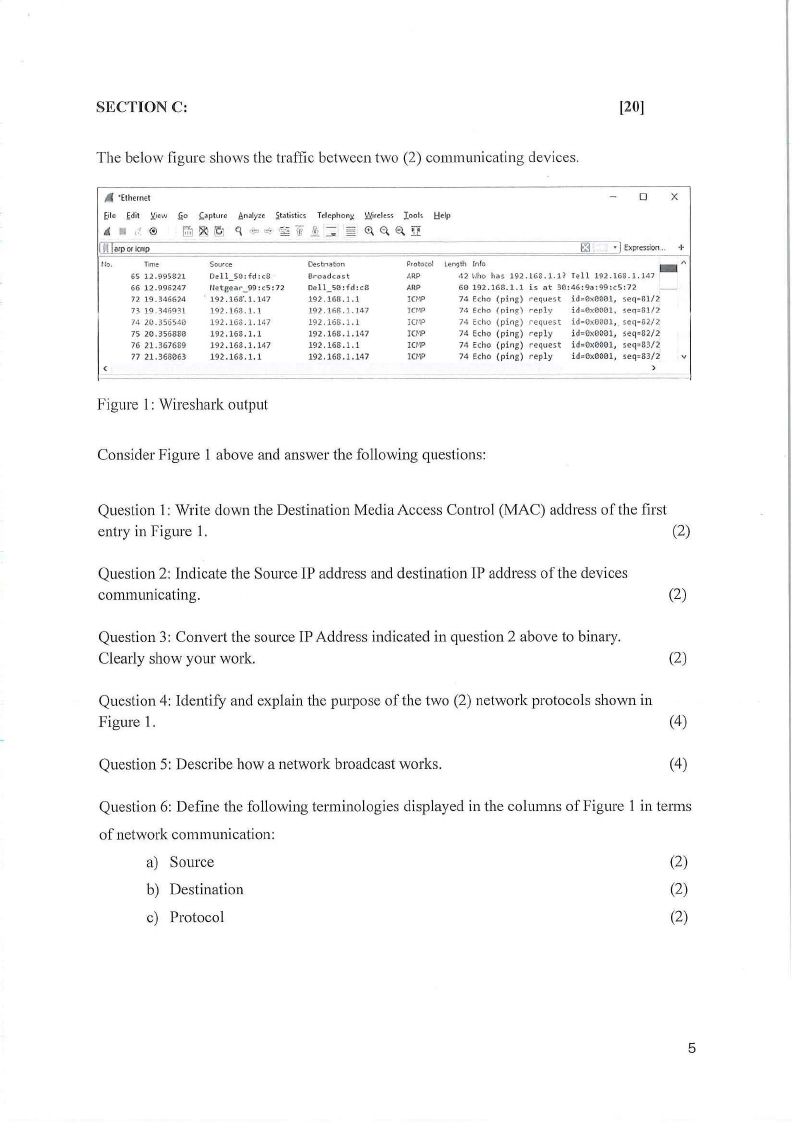
SECTION C:
[20]
The below figure shows the traffic between two (2) conum111icating devices.
·Ethemel
DX
file fdit tiew Yo
4. ,. ®
i[II arp°'lanp
l!o.
Time
65 12. 995821
66 12.996247
72 19. 346624
73 19.346931
74 20. 356540
75 20. 356880
76 21. 367669
77 21.368063
<
~apture Analyze ~tatistics Telephonx
Source
Dell - 50:fd:c8
lletgear _99: cs: 72
. 192.168".1.147
192.168.1.l
192.166.1.147
192.168.1.l
192.168.1.147
192.168.1.l
Oesbnabon
Broadca!.t
Dell_50:fd:c8
192.168.1.l
192.168.1.147
192.168.1.l
192.168.1.147
192 .168 .1. l
192.168.1.147
Wirele!is !ools !:!elp
-.. ] Expression... +
ARP
42 \\/ho has 192.16S.1.J? Tell 192.168.1.147
i\\RP
60 192.168.1.l is at 38:46:9a:99:c5:72
IO\\P
74 Echo (ping) request id•0x0001, seq•Bl/2
ICMP
74 Echo (ping) reply
id•0x0001, seq=81/2
IC/IP
74 Echo (ping) request id=Ox0OOl, seq=62/2
ICMP
74 Echo (ping) reply
id•0x00a1, seq•82/2
ICHP
74 echo (ping) request id•0x0001, seq•83/2
IC/-\\P
74 Echo (ping) reply
id•Ox000l, seq•83/2
Figure l: Wireshark output
Consider Figure l above and answer the following questions:
Question 1: Write down the Destination Media Access Control (MAC) address of the first
entry in Figure 1.
(2)
Question 2: Indicate the Source IP address and destination IP address of the devices
communicating.
(2)
Question 3: Convert the source IP Address indicated in question 2 above to binary.
Clearly show your work.
(2)
Question 4: Identify and explain the purpose of the two (2) network protocols shown in
Figure 1.
(4)
Question 5: Describe how a network broadcast works.
(4)
Question 6: Define the following terminologies displayed in the columns of Figure 1 in terms
of network communication:
a) Source
(2)
b) Destination
(2)
c) Protocol
(2)
5
 |
7 Page 7 |
▲back to top |
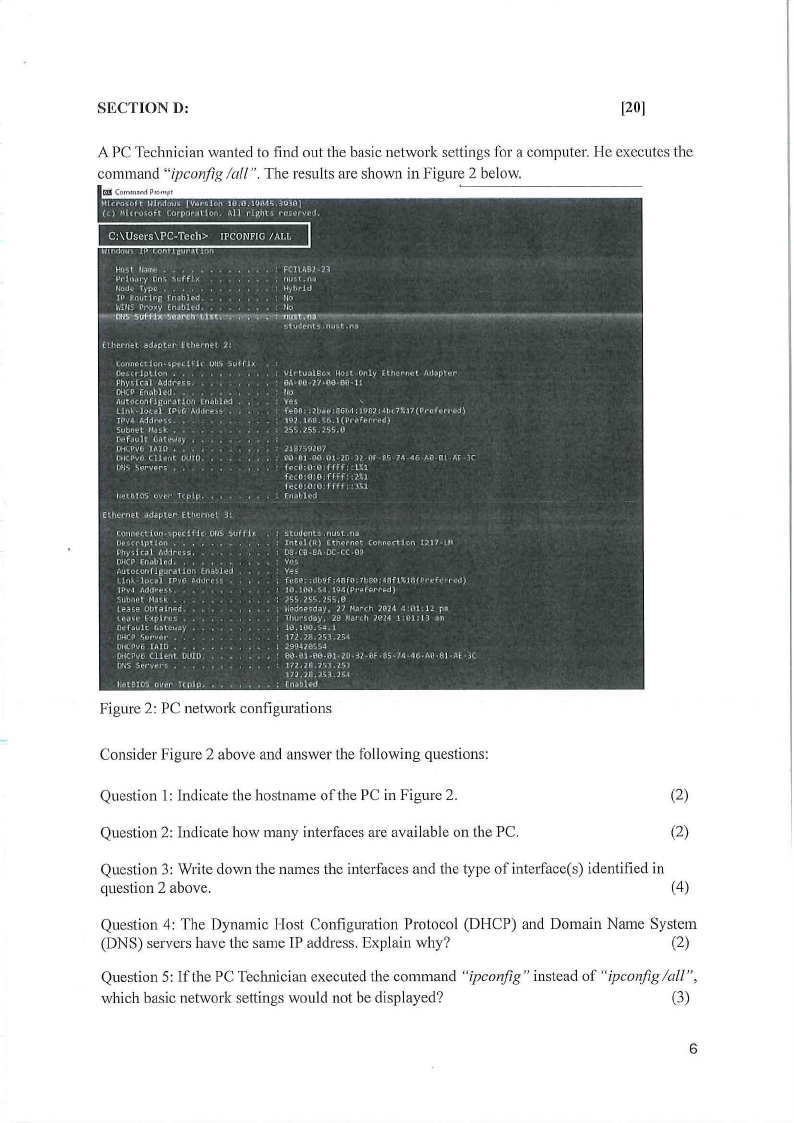
SECTIOND:
[20]
A PC Technician wanted to find out the basic network settings for a computer. He executes the
command "ipconjig /all". The results are shown in Figure 2 below.
Figure 2: PC network configurations
Consider Figure 2 above and answer the following questions:
Question 1: Indicate the hostname of the PC in Figure 2.
(2)
Question 2: Indicate how many interfaces are available on the PC.
(2)
Question 3: Write down the names the interfaces and the type of interface(s) identified in
question 2 above.
(4)
Question 4: The Dynamic Host Configuration Protocol (DHCP) and Domain Name System
(DNS) servers have the same IP address. Explain why?
(2)
Question 5: If the PC Technician executed the command "ipconfig" instead of "ipco11fig/all",
which basic network settings would not be displayed?
(3)
6
 |
8 Page 8 |
▲back to top |

Question 6: Write down the conunand the PC Technician would have to execute to identify all
the devices that the PC in Figure 2 has communicated with on the Local Area Network. (2)
Question 7: The PC in Figure 2 is connected to the Local Area Network (LAN) using
Unshielded Twisted Pair (UTP) cables.
a) Mention two (2) disadvantages of using UTP cables.
(2)
b) The PC technician proposes to his supervisor that they upgrade the Local Area
Network (LAN) by replacing UTP cables with Shielded Twisted Pair (STP) cables.
Mention three (3) advantages this change will have on the LAN.
(3)
SECTIONE:
[20]
Question 1: You are hired as a Network Administrator for a new Small Medium Enterprise
(SME) business. The ISP allocated an IP address of 172.100.32.10 /29 to the SME business.
Using the given IP address, answer the following questions and clearly show your calculations.
a) What is the Subnet Address
(2)
b) What is the Subnet Mask
(2)
c) How many network bits are borrowed from the host portion?
(2)
d) What is the number of possible subnets?
(2)
e) What is the number of usable IP addresses per subnet
(2)
f) Identify the Subnet IP address range the above-given IP address belongs to.
(2)
g) What is the Broadcast Address of the above subnet range in question (f).
(2)
h) Indicate the IP class and type of address of the above-given IP address.
(2)
i) As a network administrator, provide and explain four (4) benefits of subnetting a
network.
(4)
SECTIONF:
[10]
Answer the following questions:
Question 1: It was anticipated that by now, IPv4 addresses were expected to have depleted.
Identify and explain two (2) techniques that are utilized to preserve the availability ofIPv4
addresses to date.
(4)
Question 2: Identify and explain two (2) advantages the development of the OSI model
provides in computer networks.
(2)
Question 3: Define data integrity in network security.
(2)
---------------------T- HEEND----------------------
[100 MARKS]
7





