 |
DTN611S - DATA NETWORKS - 2ND OPP - JULY 2024 |
 |
1 Page 1 |
▲back to top |

nAmlBIA UnlVERSITY
OF SCIEnCE Ano TECHnOLOGY
Faculty of Computing and Informatics
Department of Computer Science
QUALIFICATION: BACHELOR OF COMPUTER SCIENCE
QUALIFICATION CODE: : 07BCMS,
07BAIT, 07BCCY, 07BACS
COURSE: DATA NETWORKS
DATE: JUNE
DURATION: 3 HOURS
LEVEL: 6
COURSE CODE: DTN611S
PAPER: SECOND OPPORTUNITY I
SUPPLEMENTARY
MARKS: 100
SECOND OPPORTUNITY EXAMINATION QUESTION PAPER
EXAMINER(S)
NDESHIHAFELA KAKWAMBI
MODERATOR:
LOINI IIYAMBO
THIS QUESTION PAPER CONSISTS OF 7 PAGES (Excluding this front page)
INSTRUCTIONS
1. Answer ALL the questions.
2. Write clearly and neatly.
3. Number the answers clearly.
4. When answering questions, you should be guided by the allocation of marks. Do not give
too few or too many facts in your answers.
PERMISSIBLE MATERIALS
1. Non-programmable calculator
 |
2 Page 2 |
▲back to top |

SECTION A:
[10]
Write True (T) or False (F)
Question 1: Jack is sending an email to elearning@nust.na. The email address is a user-
friendly address in communication networks.
Question 2: A device that changes the point of connection to a network is said to be wireless.
Question 3: Point-to-point is a type of network arcl1itech1rein computer networks.
Question 4: The decapsulation process happens on the side of the source network.
Question 5: Wireless Protected Access 2 (WPA2) is used for security in Wireless Fidelity.
Question 6: Servers are devices which provide services to computers on the network.
Question 7: The wide area network is the largest data network on earth.
Question 8: A switch is associated with a star network topology.
Question 9: A /17 subnetwork can be written in dotted decimal notation as 255.255.128.0
Question 10: An HTTP response message never has an empty message body.
SECTIONB:
[20]
Circle the correct answer(s).
Question 1: A user is having problems accessmg the Internet. The command "ping
www.cisco.com" is executed but fails. However, pinging the IP address of cisco with the
command "ping 198.133.219.25" is successful. What is the problem?
a. The web server is down
b. The default gateway is incorrect
c. There is a problem with DNS
d. The ARP cache needs to be cleared
Question 2: One of the advantages of a Local Area Network is that it allows
a. Accessing the internet
b. Backing up your data
c. Using the same resources
d. None of the above
1
 |
3 Page 3 |
▲back to top |

Question 3: Which statement c01Tectlydescribes the Internet?
a. lt is a network based on Ethernet technology.
b. It provides network access for mobile devices.
c. It provides connections through interconnected global networks.
d. It is a private network for all organisation with LAN and WAN connections.
Question 4: An attack by a group of compromised hosts used to distribute denial-of-service
attacks against targeted hosts is called?
a. denial-of-service attack
b. botnet attack
c. worms attack
d. None of the above
Question 5: Which protocol will return the following message "Destination Unreachable"
a. Pathping
b. Domain Name System
c. Internet Control Messaging Protocol
d. Internet Protocol
Question 6: What is the binary equivalence of the decimal number 320?
a. 111111100
b. 111011111
C. 101000111
d. 101000000
Question 7: A company is expanding its business to other countries. All branch offices must
remain connected to the corporate headquarters at all times. Which network type is required
to support this requirement?
a. Wide Area Network
b. Internet
c. Local Area Network
d. Metropolitan Area Network
Question 8: Which of the following is a goal of an ideal multiple-access protocol?
a. Empty slots
b. High overhead
c. Decentralised
d. Slow
Question 9: During the encapsulation process, what occurs at the data link layer for a PC
connected to an Ethernet network?
a. An IP address is added.
b. The logical address is added.
c. The physical address is added.
d. The process port number is added.
2
 |
4 Page 4 |
▲back to top |

Question 10: A host is transmitti1~ga broadcast packet. Which host or hosts will receive it?
a. All hosts on the internet
b. A specially defined group of hosts
c. All hosts in the same subnet
cl. The closest neighbour on the same network
Question 11: Which field in the IPv4 header is used to prevent a packet from traversing a
network endlessly?
a. Time-to-Live
b. Syn Number
c. Round Trip Time
d. Internet Protocol
Question 12: What information does the loopback test provide?
a. The NIC on the device is working correctly.
b. The device has end-to-end connectivity.
c. The Ethernet cable is working correctly.
d. The device has the correct IP address on the network.
Question 13: What statement describes the function of the Address Resolution Protocol?
a. ARP is used to discover the IP address of any host on a different network.
b. ARP is used to discover the IP address of any host on the local network.
c. ARP is used to discover the MAC address of any host on a different network.
d. ARP is used to discover the MAC address of any host on the local network.
Question 14: What will happen if the default gateway address is inc01Tectlyconfigured on a
host?
a. The switch will not forward packets initiated by the host.
b. The host will have to use ARP to determine the correct address of the default gateway.
c. The host cannot communicate with hosts in other networks.
d. A ping from the host to 127.0.0.1 would not be successful.
Question 15. What is the prefix length notation for the subnet mask 255.255.255.224?
a. /25
b. /26
C. /27
d. /28
Question 16:,Identifying the IP address associated with a specific domain name can be found
using which command?
a. Netsh
b. Nslookup
C. DNS
d. Arp -a
3
 |
5 Page 5 |
▲back to top |

Question 17: Convert the binary number 10111010 into its hexadecimal equivalent.
a. B3
b. Al
C. BA
d. lC
Question 18: The unit of information at the application layer is called?
a. Message
b. Packet
C. HTTP
d. Frame
Question 19: FTP is an acronym for?
a. File Transfer Port
b. File Transfer Protocol
c. File Transmission Pmt
d. Filtered Transmission Protocol
Question 20: Which methods are used to upload and download files on webservers?
a. Src and Dest
b. PUT And GET
c. Upload and Download
d. SYN and ACK
SECTIONC:
(20]
Figure I below shows the traffic intercepted between two (2) communicating devices.
'Ethernet
file fdit l(iew §o
! [l'l arporlcmp
No.
Tone
65 12.995821
66 12.996247
72 19.346624
73 19. 346931
74 20.356540
75 20,356880
76 21. 367689
77 21.368063
DX
f;.apture 8nalyze ~tatistics Telephoni ~ireless Iools ]:!elp
q •-cl lo- -~
::;
0. 0. @. ll
rn •] Expression... +
Source
Oell_50:fd:c8
fletgear_99:c5:72
192 .168.1.147
192.168, l. l
192.168.1.147
192.166.1,1
192.168.1.147
192.168.1. l
Oesbnation
Broadcast
Dell_SO:fd:c8
192.168.l.l
192.168.1.147
192.168. 1.1
192.168.1,147
192. 168. 1. 1
192 .168 .1.147
Protocol Length Info
-"
ARP
42 Who has 192.168.1.1? Tell 192.168.1.147
AnP
60 192.168.1.1 is at 30:46:9a:99:c5:72
ICMP
74 Echo (ping) request id~0xe001, seq•81/2
ICMP
74 Echo (ping) reply
id•0x0001, seq~81/2
IG-IP
74 Echo (pinB) request id•0x0001, seq•82/2
ICMP
74 Echo (ping) reply
id;0x0001, seq;82/2
ICMP
74 Echo (ping) request id•0X0001, seq•83/"2
ICMP
74 Echo (ping) reply
id•Ox0001, ~eq•83/2
V
Figure 1: Wireshark Output
4
 |
6 Page 6 |
▲back to top |
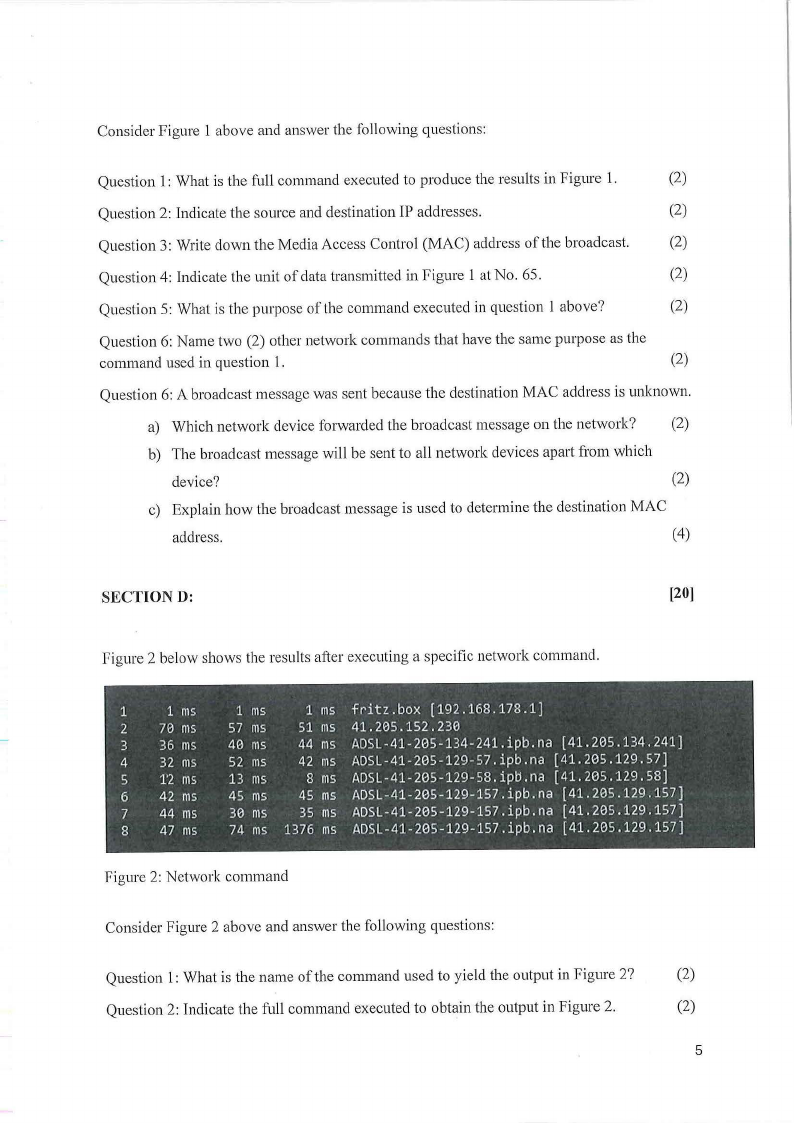
Consider Figure 1 above and answer the following questions:
Question 1: What is the full command executed to produce the results in Figure 1.
(2)
Question 2: Indicate the source and destination IP addresses.
(2)
Question 3: Write down the Media Access Control (MAC) address of the broadcast.
(2)
Question 4: Indicate the unit of data transmitted in Pigure 1 at No. 65.
(2)
Question 5: What is the purpose of the command executed in question 1 above?
(2)
Question 6: Name two (2) other network commands that have the same purpose as the
command used in question 1.
(2)
Question 6: A broadcast message was sent because the destination MAC address is unknown.
a) Which network device forwarded the broadcast message on the network?
(2)
b) The broadcast message will be sent to all network devices apart from which
device?
(2)
c) Explain how the broadcast message is used to determine the destination MAC
address.
(4)
SECTIOND:
[20]
Figure 2 below shows the results after executing a specific network command.
1
1 ms 1 ms 1 ms fritz.box (192.168.178.1)
2 70 ms 57 ms 51 ms 41.205.152.230
3 36 ms 40 ms 44 ms ADSL-41-205-134-241.ipb.na [41.205.134.241)
4 32 ms 52 ms 42 ms ADSL-41-205-129-57.ipb.na (41.205.129.57)
5 1'2 ms 13 ms 8 ms ADSL-41-205-129-58.ip~.na (41.205.129.58)
6 42 ms 45 ms 45 ms ADSL-41-205-129-157.ipb.na [41.205.129.157)
7 44 ms 30 ms 35 ms ADSL-41-205-129-157.ipb.na [41.205.129.157)
8 47 ms 74 ms 1376 ms ADSL-41-205-129-157.ipb.na [41.205.129.157)
Figure 2: Network conm1and
Consider Figure 2 above and answer the following questions:
Question 1: What is the name of the command used to yield the output in Figure 2?
(2)
Question 2: Indicate the full command executed to obtain the output in Figure 2.
(2)
5
 |
7 Page 7 |
▲back to top |

Question 3: What is the default gateway's IP address of the device that executed the
command
(2)
Question 4: What is the IP address of the destination?
(2)
Question 5: Indicate the IP address class of the destination address.
(2)
Question 6: Indicate the type ofIP address for the destination address.
(2)
Question 7: Indicate how many routers were transversed by the packet in Figure 2.
(2)
Question 8: Convert the IP address 41.205.152.230 into binary, octet by octet. Show your
work.
(3)
Question 9: Explain the purpose the command mentioned above in question 1.
(3)
SECTION E:
(20]
Question l: List the 3 types of access networks in computer networks.
(3)
Question 2: Identify the Protocol Data Unit at each layer of the TCP/IP Model.
(5)
a) Applic.ation Layer
b) Transport Layer
c) Network Layer
d) Data Link Layer
e) Physical Layer
Question 3: Mention two (2) mail access protocols that retrieve messages from the server and
state their corresponding port numbers.
(2)
Question 4: Explain the following fundamental components of a data network:
a) Protocol
(2)
b) Message
(2).
c) Host
(2)
Question 5: Name and explain two (2) techniques used in computer networks to preserve the
availability ofIPv4 addresses.
(4)
6
 |
8 Page 8 |
▲back to top |

SECTIONF:
[20]
Question 1: You are hired as a Network Administrator for a newly established company. The
ISP allocates the company a Class B network with the IP address of 172.16.0.11 /24. Calculate
the following and clearly show your work.
a) I-low many bits are reserved for the network portion?
(2)
b) How many bits are reserved for the host portion?
(2)
c) What is the subnet mask or the net\\,vork?
(2)
d) What is the lP Address of the network number?
(4)
e) What is the number of host addresses?
(2)
f) What is the number of hosts that can be configured?
(2)
g) What is the number of subnets that can be derived from the given IP address
(2)
h) What is the IP address range of the first subnet?
(2)
i) What is the broadcast IP address of the first subnet?
(2)
SECTIONF:
[10]
Question 1: The selection of a network topology is very important to any organisation
because it affects business communication services.
a) What is a network topology?
(2)
b) Identify two (2) factors that influence the selection of a network topology.
(2)
Question 2: Explain the meaning of proprietary protocols.
(2)
Question 3: What is data encapsulation?
(2)
Question 4: Mention and explain the two (2) factors of network security.
(2)
-----------------------------------------END OF EXAM-----------------------------------------
[100 MARKS]
7





