 |
CMN620S - COMMUNICATION NETWORKS - 1ST OPP - NOV 2022 |
 |
1 Page 1 |
▲back to top |
nAmlBIA unlVERSITY
OF SCIEn CE Ano TECH n OLOGY
Faculty of Computing and Informatics
Department of Computer Science
QUALIFICATION:BACHELOR OF COMPUTER SCIENCEIN CYBERSECURITY
BACHELOR OF COMPTER SCIENCE
QUALIFICATIONCODE: 07BCCS; 07BACS
LEVEL: 7
COURSE: COMMUNICATION NETWORKS
COURSECODE: CMN620S
DATE: NOVEMBER 2022
SESSION: 1
DURATION: 2 HOURS 30 MINUTES
MARKS: 70
EXAMINER(S)
MODERATOR:
FIRSTOPPORTUNITYEXAMINATION QUESTION PAPER
MR. NASIMANE EKANDJO
DR. MERCY CHITAURO
MS. LOINI IIYAMBO
MR. EDWARD NEPOLO
THIS QUESTION PAPERCONSISTSOF 5 PAGES
(Excluding this front page)
INSTRUCTIONS
1. Answer ALL the questions.
2. Write clearly and neatly.
3. Number the answers clearly.
4. When answering questions you should be guided by the allocation of
marks. Do not give too few or too many facts in your answers.
PERMISSIBLEMATERIALS
1. Non-programmable calculator.
 |
2 Page 2 |
▲back to top |

Question 1
Indicate whether the following statements are true or false.
[4]
1.1 RIP is a link state algorithm used to calculate routes within a network.
1.2 The speed of TCP is slower than UDP.
1.3 Without using a router, devices in different VLANs cannot communicate with one
another.
1.4 The router to connect VLANs is connected to a switch port in trunk mode.
1.5 ARP is a protocol that is used to route packets with unkown destination.
Question 2
Choose the correct answer from the questions below:
[6]
2.1 What is the valid host range is the IP Address 192.168.187.233 / 27 from?
a) 192.168.187.225 to 192.168.187.254
b) 192.168.187.193 to 192.168.187.224
c) 192.168.187.129 to 192.168.187.191
d) 192.168.187.65 to 192.168.187.95
2.2 If the subnet mask is 255.255.255.224, which of the following will be the broadcast
mask address?
a) 202.15.19.127
b) 202.15.19.63
c) Both A and B
d) None of the above
2.3 Which of the following statements are advantages of VLANs. (Choose two)
a) VLANs can greatly simplify adding, moving or changing hosts on the
network.
b) VLANs utilises packet filtering to enhance security.
c) VLANs provide a method of conserving IP addresses in large networks.
d) VLANs establish broadcast domains in switched networks.
e) VLANs provide a low-latency internetworking alternative to routed
networks.
Page 1 of 5
 |
3 Page 3 |
▲back to top |

2.4 Which of the following command will save the router's configurations to NVRAM?
a) Router#save run start
b) Router#copy run start
c) Router#copy start run
d) Router#reload run start
Question 3
Define the following concepts/key words used in communication networks.
3.1 VLAN trunk port
[2]
3.2 Network layer data plane
[2]
Question 4
4.1 Explain the concept of circuit switching.
[2]
4.2 State two advantages of circuit switching.
[2]
4.3 Give an example where circuit switching can be used/more suitable.
[1]
Question 5
5.1 Describe how a link-state routing algorithm works.
[3]
5.2 Explain what happens when the link costs changes in a network with routers
running distance vector algorithm.
[3]
Question 6
Consider the router extract below:
Line 1) Router>enable
Line 2) Router#conf igure
Line3) Router(config)#line
Line 4) Router ( conf ig-line)
Line 5) Router (config-line)
Line6) Router(config)#enable
terminal
vty O 9
#login
#exit
secret
crnn 2022
6.1 What is the purpose of the command in line 3?
[2]
6.2 What is the purpose of the command in line 4?
[1]
6.3 What password (line 6) has been configured here? Where will you be prompted to
enter this password?
[2]
Page 2 of 5
 |
4 Page 4 |
▲back to top |
Question 7
7.1 Explain three benefits of utilising VLANs in a network design.
[3]
7.2 Which protocol is used to configure trunking on a switch?
[2]
7.3 Mention the main type of encapsulation trunking protocol that is an IEEEstandard.
[2]
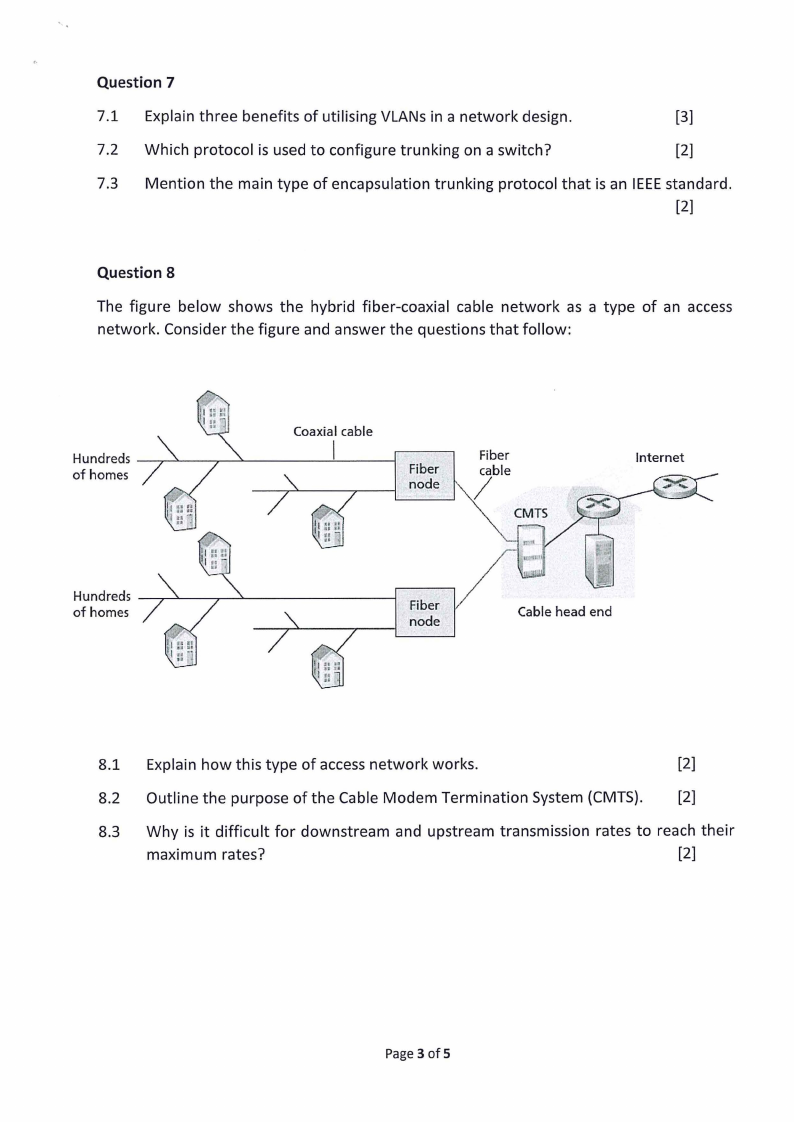
Question 8
The figure below shows the hybrid fiber-coaxial cable network as a type of an access
network. Consider the figure and answer the questions that follow:
Coaxial cable
Hundreds --,,-~--,,-~----~! -----,
Fiber
of homes
Fiber
node
cable
I
Internet
Hundreds --,,-->-----,,-__,__
of homes
_______
_
Fiber ,
node
Cable head end
8.1 Explain how this type of access network works.
[2]
8.2 Outline the purpose of the Cable Modem Termination System (CMTS). [2]
8.3 Why is it difficult for downstream and upstream transmission rates to reach their
maximum rates?
[2]
Page 3 of 5
 |
5 Page 5 |
▲back to top |
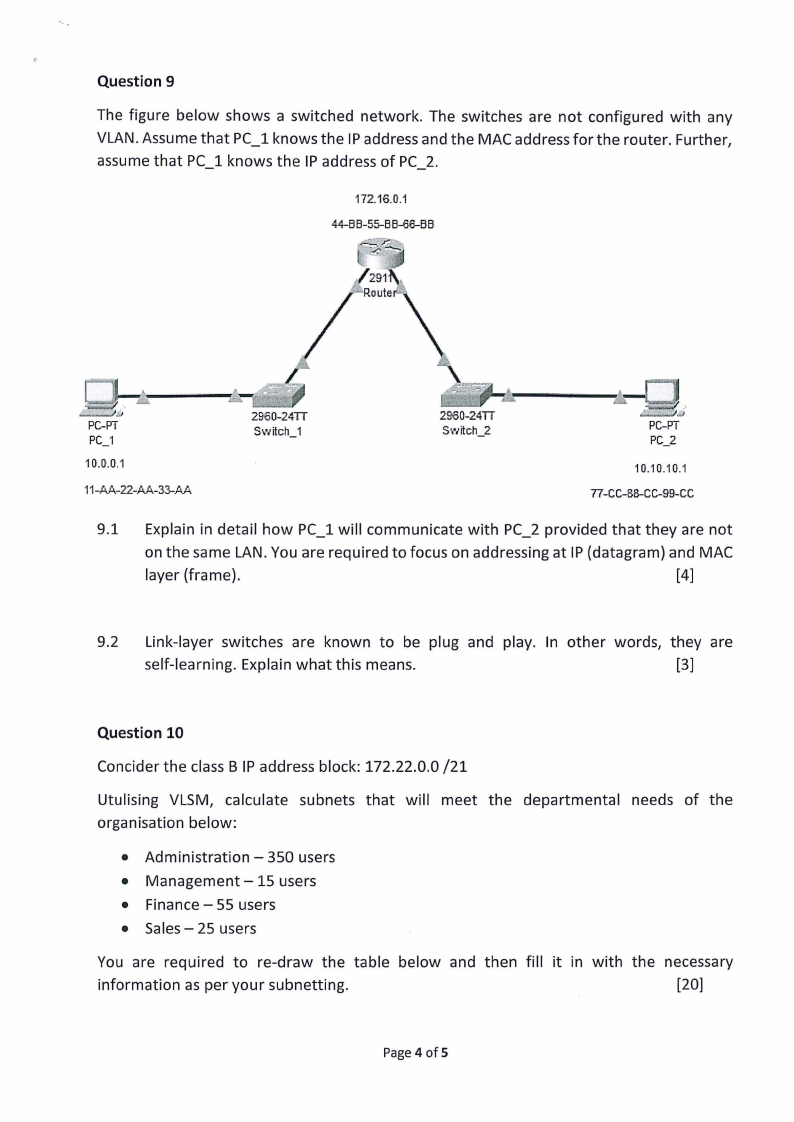
Question 9
The figure below shows a switched network. The switches are not configured with any
VLAN. Assume that PC_l knows the IP address and the MAC address for the router. Further,
assume that PC_l knows the IP address of PC_2.
172.16.0.1
44-BB-55-BB--66--BB
~.u·
PC-PT
PC_1
10.0.0.1
11-AA-22-AA-33-AA
2960-24TT
Switch_1
29'60-24TT
Switch_2
10.10.10.1
77-CC-BS-CC-99-CC
9.1 Explain in detail how PC_l will communicate with PC_2 provided that they are not
on the same LAN. You are required to focus on addressing at IP (datagram) and MAC
layer (frame).
[4]
9.2 Link-layer switches are known to be plug and play. In other words, they are
self-learning. Explain what this means.
[3]
Question 10
Concider the class B IP address block: 172.22.0.0 /21
Utulising VLSM, calculate subnets that will meet the departmental needs of the
organisation below:
• Administration - 350 users
• Management - 15 users
• Finance - 55 users
• Sales- 25 users
You are required to re-draw the table below and then fill it in with the necessary
information as per your subnetting.
(20]
Page 4 of 5
 |
6 Page 6 |
▲back to top |
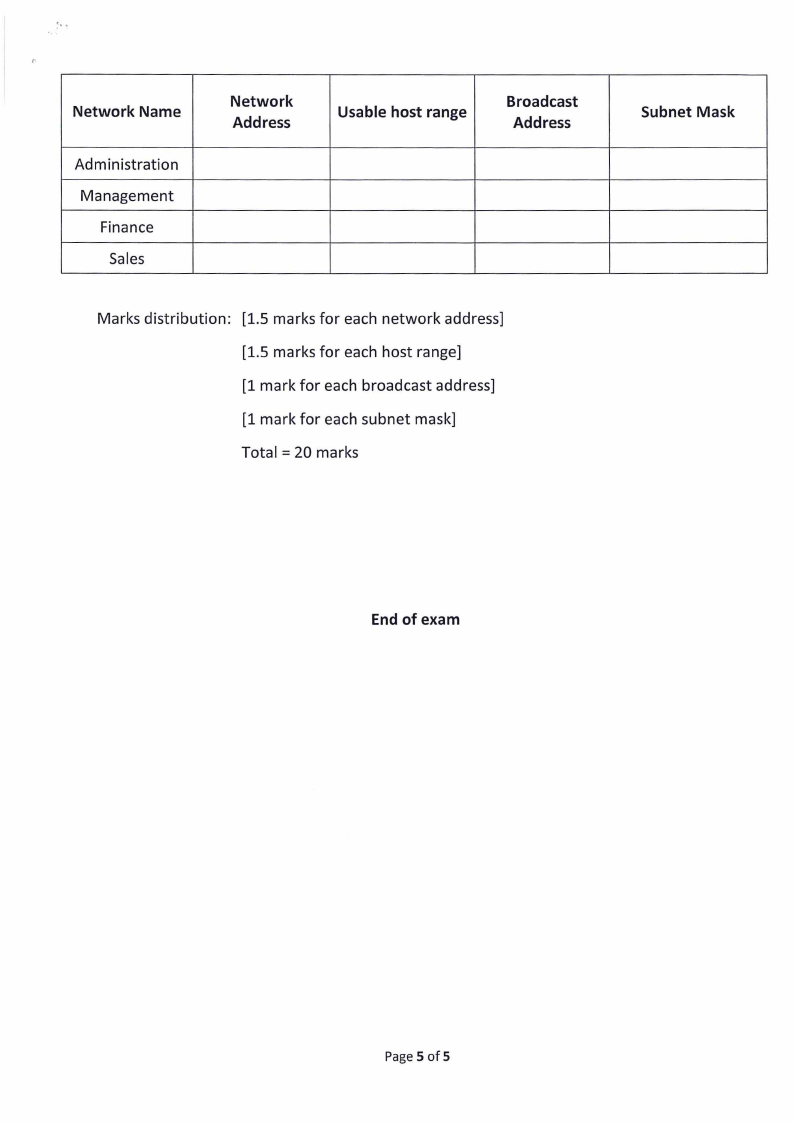
Network Name
Administration
Management
Finance
Sales
Network
Address
Usable host range
Broadcast
Address
Marks distribution: [1.5 marks for each network address]
[1.5 marks for each host range]
[1 mark for each broadcast address]
[1 mark for each subnet mask]
Total= 20 marks
Subnet Mask
End of exam
Page 5 of 5





