 |
OPS611S - OPERATING SYSTEMS - 2ND OPP - JULY 2024 |
 |
1 Page 1 |
▲back to top |
n Am I BIA u n IVERs ITY
OFSCIEnCEAnDTECHn OLOGY
FACULTYOF COMPUTING AND INFORMATICS
DEPARTMENTOF COMPUTER SCIENCE
QUALIFICATION:BACHELOROF COMPUTER SCIENCE(SYSTEMSADMINISTRATION)
QUALIFICATIONCODE:07BCMS
LEVEL6:
COURSE:Operating Systems
COURSECODE:OPS611S
DATE:July 2024
SESSION:2
DURATION:3 hours
MARKS:100
SECONDOPPORTUNITY/ SUPPLEMENTARYEXAMINATIONQUESTIONPAPER
EXAMINER(S)
FRANS HAINGURA
MODERATOR:
LOIN IIYAMBO
THISQUESTIONPAPERCONSISTSOF 5 PAGES
(Excluding this front page)
INSTRUCTIONS
1. Answer ALL the questions.
2. Write clearly and neatly.
3. Number the answers clearly.
4. When answering questions you should be guided by the allocation of marks
in [ ]. Do not give too few or too many facts in your answers.
PERMISSIBLE
1. Non programmable Scientific Calculator.
Page 1 of 6
 |
2 Page 2 |
▲back to top |

SECTION A (MULTIPLE CHOICE) 20 MARKS
1. When a job is accepted by the system, it's put on __ and placed in a queue.
[1]
a. RUNNING
b. WAITING
c. HOLD/ NEW
d. READY
2. Which of the following statements is true regarding CPU context switching?
[1]
a. Register values for the currently running process are all reset.
b. Register values for the currently running process are stored into its PCB
c. Register values of the new running state are not loaded into the CPU
d. None of the above
3. Assume that jobs A-D arrive in the READY queue in quick succession and have the CPU cycle
requirements listed below. Using the SRT algorithm, the average turnaround time is __ . [1]
Arrival time: 0 1 2 3
Job:
ABC D
CPU cycle: 6 3 1 4
a. 2.5
b. 6.15
C. 7.75
d. 6.25
4. Some systems use a strategy known as __ to increase the priority of jobs that have been in
the system for an unusually long time to expedite their exit.
[1]
a. Logging
b. Preempting
c. Aging
d. Accelerated priority
5. When the operating system detects a nonrecoverable error, the following step is performed first
by the interrupt handler: __ .
[1]
a. The state of the interrupted process is saved
b. The type of interrupt is described and stored
c. The interrupt is processed
d. The processor resumes operation
6. A livelock can be caused by two processes accessing different areas of the same disk.
[1]
a. False
b. True
Page 2 of 6
 |
3 Page 3 |
▲back to top |

7. If locks are not used to preserve data integrity, the updated records in a database may include
only some of the data and their contents depend on the order in which each process finishes its
execution.
(1]
a. True
b. False
8. Database locking should be done only at the level of the entire database.
(1]
a. True
b. False
9. When using a directed graph to model a system, if there's a cycle in the graph, then there is a
deadlock involving the processes and the multi-instance resources shown in the cycle.
(1]
a. False
b. True
10. According to the Banker's Algorithm, an unsafe state always leads to deadlock.
(1]
a. True
b. False
11. On an optical disc, all sectors are __ .
(1]
a. of varying sizes depending upon where you are on the disc
b. larger as you move to the edge
c. smaller as you move to the edge
d. of the same size throughout the disc
12. Device management principles are changing rapidly to accommodate cloud computing.
[1]
a. False
b. True
13. Seek time is the most important characteristic of a fixed-head disk drive.
(1]
a. True
b. False
14. In the SCAN device-scheduling algorithm, any requests that arrive while the arm is in motion are
grouped for the arm's next sweep.
(1]
a. False
b. True
15. The job of the 1/0 control unit is to keep up with the 1/0 requests from the CPU and pass them
down the line to the appropriate control unit.
(1]
a. True
b. False
Page 3 of 6
 |
4 Page 4 |
▲back to top |

16. ___
are special files with listings of file names and their attributes.
[1]
a. Databases
b. Directories
c. Programs
d. Data files
17. The computer system __ a file by activating the appropriate secondary storage device and
loading the file into memory while updating its records of who is using that file.
[1]
a. Creates
b. Formats
c. Allocates
d. Configures
18. A file's ___ file name includes all path information for that file.
[1]
a. Extended
b. Absolute
c. Relative
d. Long-form
19. A(n) __ file name is the name that differentiates a file from other files in the same directory. [1]
a. Absolute
b. Relative
c. Short-form
d. Directory
20. As long as users refer to files in the __
absolute filename.
a. Root
b. Main
c. Home
d. Working
directory, they can access the files without entering the
[1]
SECTION B (THEORY) 20 MARKS
1. Name and explain three features of an Operating System.
[6]
2. How does a Batch System differ from an Interactive System
[2]
3. Differentiate between preemptive and non-preemptive scheduling policies with examples. [4]
4. Differentiate between a time quantum expiration interrupt and an illegal arithmetic operation
interrupt.
[2]
5. What are the prerequisite conditions of a deadlock?
[4]
6. Briefly explain the difference between buffering and blocking.
[2]
Page 4 of 6
 |
5 Page 5 |
▲back to top |
SECTION C (ALGORITHMS AND COMPUTATIONS) 60 MARKS
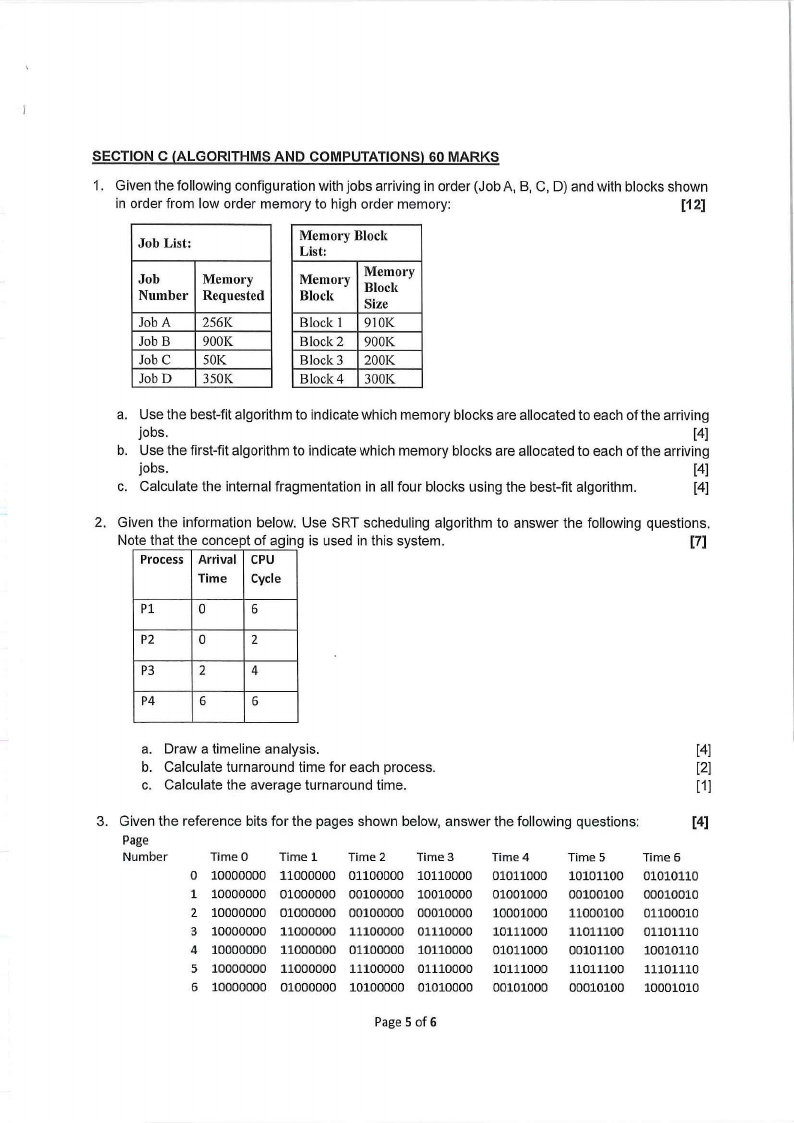
1. Given the following configuration with jobs arriving in order (Job A, B, C, D) and with blocks shown
in order from low order memory to high order memory:
[12]
Job List:
Job
Memory
Number Requested
Job A
Job B
Job C
Job D
256K
900K
SOK
350K
Memory Block
List:
Memory
Block
Memory
Block
Size
Block I 910K
Block 2 900K
Block3 200K
Block 4 300K
a. Use the best-fit algorithm to indicate which memory blocks are allocated to each of the arriving
jobs.
[4]
b. Use the first-fit algorithm to indicate which memory blocks are allocated to each of the arriving
jobs.
[4]
c. Calculate the internal fragmentation in all four blocks using the best-fit algorithm.
[4]
2. Given the information below. Use SRT scheduling algorithm to answer the following questions.
Note that the concept of aging is used in this system.
[7]
Process Arrival CPU
Time Cycle
Pl
0
6
P2
0
2
P3
2
4
P4
6
6
a. Draw a timeline analysis.
[4]
b. Calculate turnaround time for each process.
[2]
C. Calculate the average turnaround time.
[1l
3. Given the reference bits for the pages shown below, answer the following questions:
[4]
Page
Number
Time0
Timel
Time2
Time3
Time4
Times
Time6
0 10000000 11000000 01100000 10110000 01011000 10101100 01010110
1 10000000 01000000 00100000 10010000 01001000 00100100 00010010
2 10000000 01000000 00100000 00010000 10001000 11000100 01100010
3 10000000 11000000 11100000 01110000 10111000 11011100 01101110
4 10000000 11000000 01100000 10110000 01011000 00101100 10010110
5 10000000 11000000 11100000 01110000 10111000 11011100 11101110
6 10000000 01000000 10100000 01010000 00101000 00010100 10001010
Page 5 of6
 |
6 Page 6 |
▲back to top |
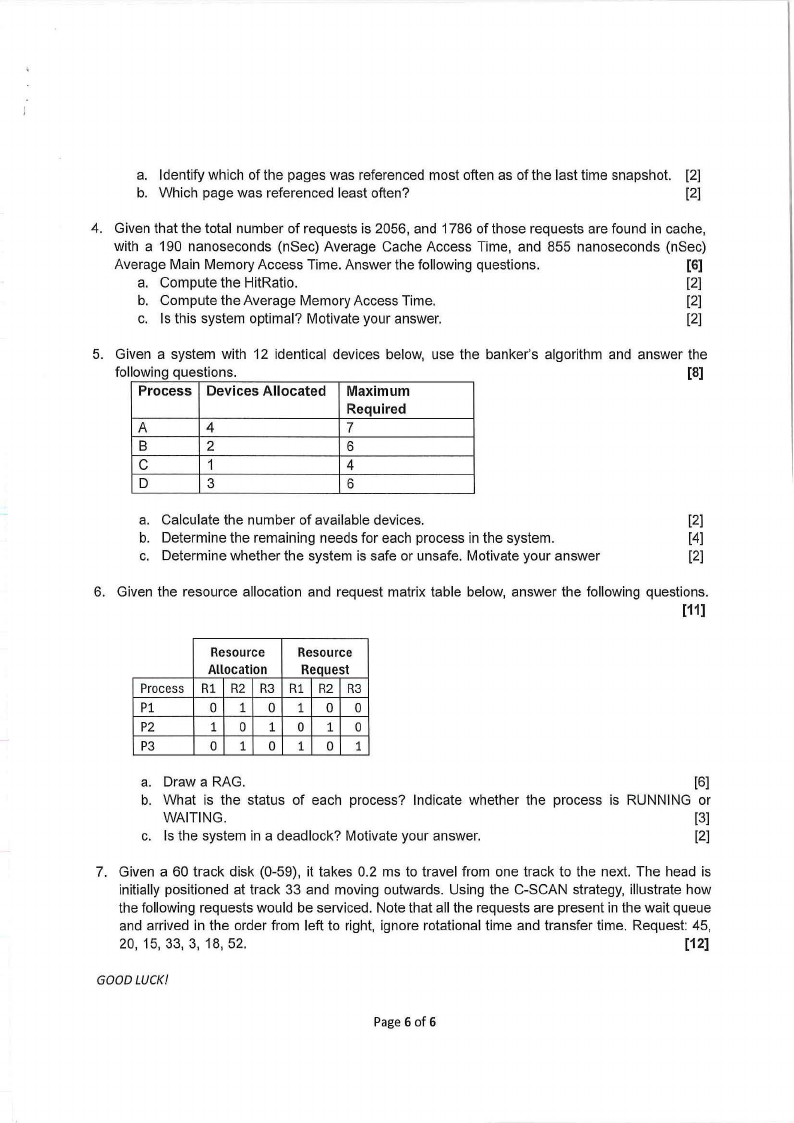
a. Identify which of the pages was referenced most often as of the last time snapshot. [2]
b. Which page was referenced least often?
[2]
4. Given that the total number of requests is 2056, and 1786 of those requests are found in cache,
with a 190 nanoseconds (nSec) Average Cache Access Time, and 855 nanoseconds (nSec)
Average Main Memory Access Time. Answer the following questions.
[6)
a. Compute the HitRatio.
[2]
b. Compute the Average Memory Access Time.
[2]
c. Is this system optimal? Motivate your answer.
[2]
5. Given a system with 12 identical devices below, use the banker's algorithm and answer the
following questions.
[8]
Process Devices Allocated Maximum
Required
A
4
7
B
2
6
C
1
4
D
3
6
a. Calculate the number of available devices.
[2]
b. Determine the remaining needs for each process in the system.
[4]
c. Determine whether the system is safe or unsafe. Motivate your answer
[2]
6. Given the resource allocation and request matrix table below, answer the following questions.
[11]
Resource Resource
Allocation Request
Process Rl R2 R3 Rl R2 R3
Pl
0 10 100
P2
10 10 10
P3
0 10101
a. Draw a RAG.
[6]
b. What is the status of each process? Indicate whether the process is RUNNING or
WAITING.
[3]
c. Is the system in a deadlock? Motivate your answer.
[2]
7. Given a 60 track disk (0-59), it takes 0.2 ms to travel from one track to the next. The head is
initially positioned at track 33 and moving outwards. Using the C-SCAN strategy, illustrate how
the following requests would be serviced. Note that all the requests are present in the wait queue
and arrived in the order from left to right, ignore rotational time and transfer time. Request: 45,
20, 15, 33, 3, 18, 52.
[12)
GOOD LUCK!
Page 6 of 6





