 |
BIS521S - BUISNESS INFORMATION SYSTEMS 1B - 1ST OPP - NOVEMBER 2023 |
 |
1 Page 1 |
▲back to top |

n Arn I BI A unIVER sITY
OF SCIEnCE Ano TECHnOLOGY
FACULTY OF COMMERCE, HUMAN SCIENCESAND EDUCATION
DEPARTMENT OF GOVERNNANCE AND MANAGEMENT SCIENCES
QUALIFICATION: Bachelor of Business and Information Administration
QUALIFICATION CODE: 07BBIA
LEVEL: 5
COURSE CODE: 8IS521S
COURSE NAME: Business Information Systems 18
SESSION: November 2023
PAPER: Theory (Paper 1)
DURATION: 2 Hours
MARKS: 100
EXAMINER{S}
FIRST OPPORTUNITY EXAMINATION QUESTION PAPER
Ms Ester Vaino
MODERATOR: Ms Petrina Witbeen
INSTRUCTIONS
1. You have to answer ALL the questions.
2. Read questions carefully before answering.
3. Please number your answers clearly.
4. Make sure your student number appears on the answering script.
PERMISSIBLE MATERIALS
1. Pen, pencil, ruler and eraser
THIS QUESTION PAPER CONSISTS OF 5 PAGES (Including this front page)
 |
2 Page 2 |
▲back to top |

SECTION A
QUESTION 1
Please answer the following questions and indicate if it is true or false.
[30 MARKS]
[10 MARKS]
1.1 A mobile printer is a big heavy, battery-powered printer that allows a mobile user to print
from a laptop, smartphone, or another mobile device while travelling.
1.2 A digital camera is a hardware device that takes pictures like a regular camera but stores the
image as data instead of printing it to film.
1.3 A touchpad is a small, hard, square pointing device that's sensitive to pressure and motion.
1.4 Another name for a quick response code is a 2-D bar code.
1.5 Audio includes music, speech or any other sound.
1.6 Video input Is the process of capturing full-motion images and storing them on a computer
or mobile device's storage medium.
1.7 With motion input, users can guide on-screen elements using ground gestures.
1.8 The Nintendo's Wii game is blue tooth enabled.
1.9 Cable-connected speakers are also considered as input peripheral devices of a computer
system, as the input is sound or audio.
1.10 An interactive whiteboard is an instructional tool that allows computer images to be
displayed onto a board using an image projector.
QUESTION 2
Indicate and briefly explain the following abbreviations:
[10 MARKS]
2.1 VOiP
2.2 NFC:
2.3 SSD:
2.4 CPU:
2.5 CCD:
2.6 GUI
2.7 DPI:
2.8 ROM:
2.9 PPM
2.10 MBps
2
 |
3 Page 3 |
▲back to top |
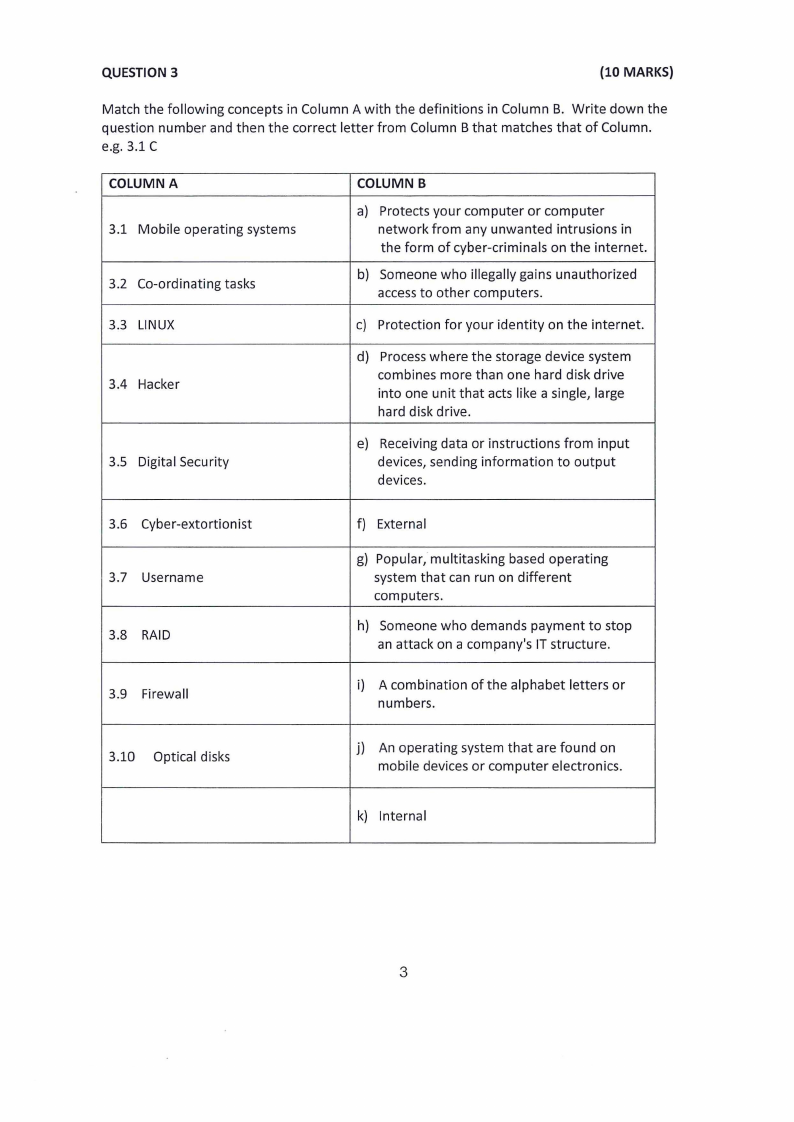
QUESTION 3
(10 MARKS)
Match the following concepts in Column A with the definitions in Column B. Write down the
question number and then the correct letter from Column B that matches that of Column.
e.g. 3.1 C
COLUMN A
3.1 Mobile operating systems
3.2 Co-ordinating tasks
3.3 LINUX
3.4 Hacker
3.5 Digital Security
COLUMN B
a) Protects your computer or computer
network from any unwanted intrusions in
the form of cyber-criminals on the internet.
b) Someone who illegally gains unauthorized
accessto other computers.
c) Protection for your identity on the internet.
d) Process where the storage device system
combines more than one hard disk drive
into one unit that acts like a single, large
hard disk drive.
e) Receiving data or instructions from input
devices, sending information to output
devices.
3.6 Cyber-extortionist
3.7 Username
3.8 RAID
3.9 Firewall
f) External
g) Popular, multitasking based operating
system that can run on different
computers.
h) Someone who demands payment to stop
an attack on a company's IT structure.
i) A combination of the alphabet letters or
numbers.
3.10 Optical disks
j) An operating system that are found on
mobile devices or computer electronics.
k) Internal
3
 |
4 Page 4 |
▲back to top |

QUESTION 4 - DEFINE THE FOLLOWING TERMS:
4.1. Output
[10 MARKS]
4.2 Graphics
4.3 Instructions
4.4 Input
4.5 Information
SECTION B
QUESTION 5 - STRUCTURED QUESTIONS
[30 MARKS]
5.1 Explain why you would need to set up a firewall on your computer.
(4)
5.2 Briefly discuss what an interactive whiteboard is and give a practical example of where it can
be used.
(4)
5.3 State and explain four (4) methods of security theft.
(8)
5.4 List six (6) of the advantages of Solid-State Drives.
(6)
5.5 What exactly does access time measure?
(2)
5.6 Name and explain the different ways of shutting down your PC.
(6)
5.7 Identify and briefly explain the two (2) types of encryption methods in the information
technology industry.
(4)
5.8 If more than one user connects to a printer, we call it a printer?
(1)
TOTAL: 100 Marks
4





