 |
BIS521S - BUSINESS INFORMATION SYSTEMS 1B - 2ND OPP - JANUARY 2023 |
 |
1 Page 1 |
▲back to top |

nAm I BIA un IVE RSITY
OF SCIEnCE Ano TECHn OLOGY
FACULTYOF COMMERCE, HUMAN SCIENCES& EDUCATION
DEPARTMENTOF GOVERNANCE& MANAGEMENT SCIENCES
QUALIFICATION: Bachelor of Business and Information Administration
QUALIFICATIONCODE: 07BBIA
COURSECODE: Bl5521S
LEVEL: 5
COURSENAME: Business Information Systems 1B
SESSION:January 2023
PAPER:Theory
DURATION: 2 Hours
MARKS: 100
2nd OPPORTUNITYEXAMINATION QUESTION PAPER
EXAMINER(S} Ms. 5. Klaassen
Ms. A. Schroeder
MODERATOR: Dr. N. Angula
INSTRUCTIONS
1. Answer ALL the questions.
2. Detach page 2 from your question paper and insert it in your answer script.
3. Read questions carefully before answering.
4. Please number your answers clearly.
5. Make sure your student number appears on the answering script.
PERMISSIBLEMATERIALS
1. Pen, pencil, ruler and eraser
THIS QUESTION PAPERCONSISTSOF 8 PAGES(Including this front page)
 |
2 Page 2 |
▲back to top |

QUESTION1: MULTIPLECHOICEQUESTIONS
[20]
Choose the letter from the options that best completes the following sentences.
Use the answer sheet on page 2 and detach it from the question paper then insert in the examinations
answer script.
1.1 Uses of voice input include:
A. Internet messaging that supports voice conversations
B. VOiP - enables users to make calls over the internet. To make a call, a telephone is connected to
a network cable, rather than a phone line or a call is made over a computer. Skype is a popular
example
C. Video calls
D. All the above
1.2
____
cables are used for audio/video transmission.
A. DVI
B. HTTP
C. HDMI
D. DVD
1.3 ____
scanners identify a person by taking measurements of a person's
_____
For
example, the distance between the person's chin, eyes, nose, and mouth. What is the missing word?
A. Hand
B. Face
C. Nose
D. Mouth
1.4 Identify the equipment in the picture underneath.
A. Barcode reader
B. Flatbed scanner
C. RFIDreader
D. None of the above
1.5 The most common method of entering text and numerical data into a computer system is using a
A. Plotter
B. Printer
C. Keyboard
D. Scanner
3
 |
3 Page 3 |
▲back to top |

1.6 ___ protects your computer or computer network from any unwanted intrusion in the form of
cyber-criminals on the internet?
A. Hardware
B. Firewall
C. Home network
D. Software
E. Privacy
1.7 __ is a type of malware that affects or infects a computer by altering the way the computer
operates without the user's knowledge.
A. Worm
B. Trojan horse
C. Virus
D. Malware
E. Spyware
1.8 Ensures that a user's information is protected and only allowing only an authorised party to view it.
A. Malware
B. Output device
C. Storage device
D. Encryption
E. Software
1.9 __ refers to the illegal distribution of software or illegal use of software if the software is
protected by copyright.
A. Information piracy
B. Privacy laws
C. Software piracy
D. Intellectual property rights
E. Digital certificate
1.10 Banks have introduced a two-step verification process to protect the financial information of their
clients. An OTP is sent to the user's mobile device. What does OTP stand for?
A. Over Time Pin
B. Open Token Pin
C. One Time Pin
D. Over Time Password
E. One Time Password
1.11 The main memory of the computer is called __
A. RAM
B. ROM
C. Virtual memory
D. GUI
1.12 __ is an example of cloud storage.
A. Micro Soft Word
B. Virtual Storage
C. Google Drive
D. Solid State Drive
4
 |
4 Page 4 |
▲back to top |

1.13 Before you can install any other software, you need __
A. A network
B. Memory
C. DVD's
D. Operating System
1.14 The part of the hard disk where information is stored or retrieved is called a __
A. Platter
B. Track
C. Cluster
D. Head
1.15 __ area small text file that a web server stores on your computer. It contains data about you like
your username, postal code, and viewing preferences.
A. Spyware
B. Cookies
C. Adware
D. Phishing
1.16 The speed of storage devices and memory is defined by accesstime. Accesstime measures __
A. The length of a movie
B. The speed of a game
C. The amount of time it takes to locate an item on a storage device
D. How fast the network is
1.17 Storage devices store information ___ _
A. Permanently
B. While the computer is on
C. When it is formatted
D. In different compartments
1.18 What device is shown in the picture? ji..
=,,.
A. 3-D printer
B. Touch Screen
C. Data printer
D. Plotter
1.19 All university students should guard against the practice of taking someone else's work or ideas
and passing them off as their own, as it refers to __ _
A. Cyber-crime
B. Encryption
C. Plagiarism
D. Protection
1.20.
This memory is extra memory and it's a small section of a hard disk space that is set up to imitate the
computer's RAM.
A. Virtual memory
B. Cache memory
C. Permanent memory
D. Volatile memory
5
 |
5 Page 5 |
▲back to top |

QUESTION 2: SHORT ANSWER QUESTIONS
lOx 2
(20)
Insert the correct term/phrase in the open space provided.
2.1 ___ is a general term used to describe the pain felt in muscles, nerves and tendons caused by
repetitive movement and overuse.
2.2 ___
are commands that the user gives to the computer by means of using an input device.
2.3 __ refers to a set of programmes that coordinate all the activities among the computer hardware
devices and software programmes on a computer.
2.4 ___ devices read text printed with magnetised ink and converts characters into a form that the
computer can process.
2.5 __ refers to the time it takes to display an image or video on the screen.
2.6 ___
is an instructional tool that allows computer images to be displayed onto a board using a
data projector.
2.7 __ are available in black-and-white or colour and are more expensive than inkjet printers but
print at a faster speed than ink-jet printers.
2.8 ____ reads hand-drawn marks such as small circles or rectangles on paper or electronically.
2.9 ___ is small metal or plastic device that looks like a tiny pen but uses pressure instead of ink.
2.10 ____
is a flatbed scanner that is composed of a glass pane under which there is a bright light
which illuminates the pane, and a moving optical array in CCDscanning.
6
 |
6 Page 6 |
▲back to top |
QUESTION 3: STRUCTURED QUESTIONS
[12)
3.1 John bought himself a computer recently and has come to you for advice on which keyboard is the
best option between an "ergonomic keyboard" and a "gaming keyboard".
(6)
3.2 Mention the three (3) basic types of wireless connection available to uses.
(6)
QUESTION 4: STRUCTURED QUESTIONS
[12)
4.1 Name and explain between the "audio" and "video" basic two (2) different types of output. (4)
4.2 Discussfour (4) characteristics of a mobile printer.
(8)
QUESTION 5: STRUCTURED QUESTIONS
[12)
5.1 Hard drives can be internal or external to the computer device. Discussfour (4) advantages of
external hard drives for users.
(8)
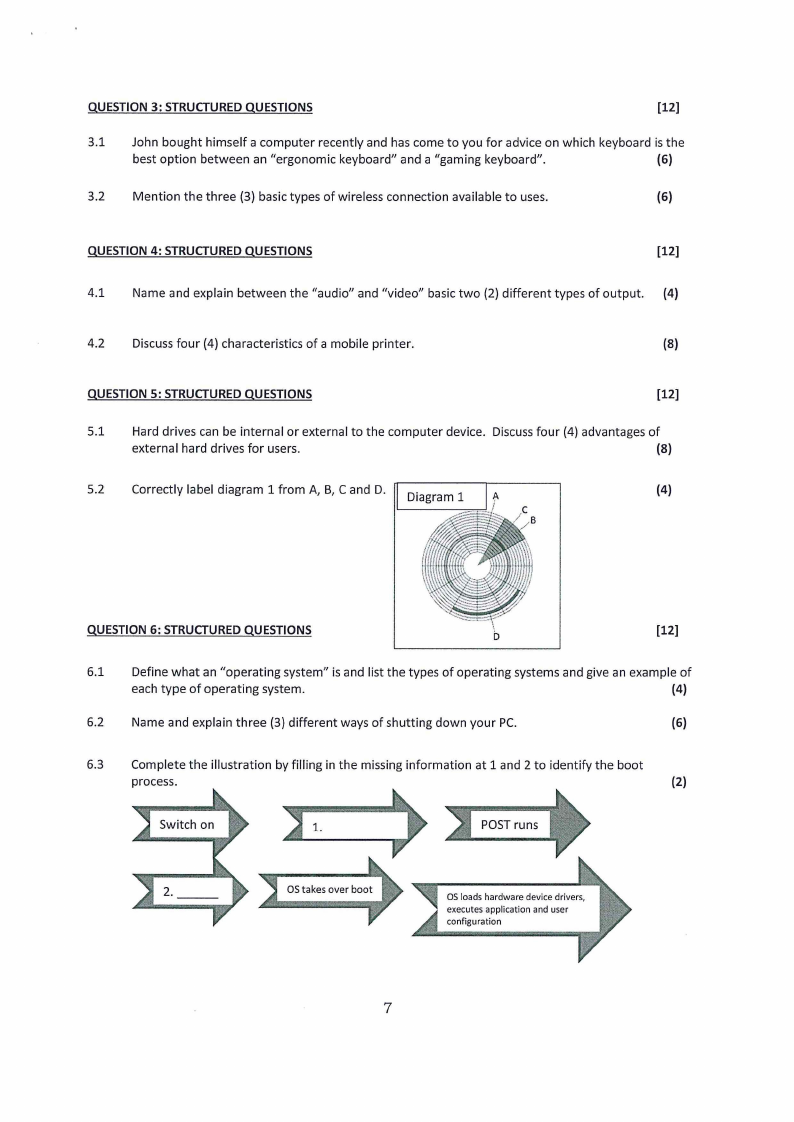
5.2
Correctly label diagram 1 from A, B, C and D. Diagra
(4)
QUESTION 6: STRUCTURED QUESTIONS
[12)
6.1 Define what an "operating system" is and list the types of operating systems and give an example of
each type of operating system.
(4)
6.2 Name and explain three (3) different ways of shutting down your PC.
(6)
6.3 Complete the illustration by filling in the missing information at 1 and 2 to identify the boot
process.
(2)
POSTruns
OS loads hardware device drivers,
executes application and user
configuration
7
 |
7 Page 7 |
▲back to top |

QUESTION 7: STRUCTURED QUESTIONS
[12]
7.1 Name and discuss any five (5) offenders of cybercrime.
(10)
7.2 Identify and briefly explain the two (2) types of encryption methods in the information technology
industry.
(2)
8
 |
8 Page 8 |
▲back to top |
Detach page 2 from your question paper and insert it in your answer script.
STUDENTNO:______
SURNAME& INITIALS:_____
QUESTION1: MULTIPLECHOICEQUESTIONSANSWERSHEET
_ GROUP:
Full-time
[20]
GROUP:
Distance
Choose the letter from the options that best completes the following sentences by inserting a cross
at the correct letter.
1.1
A
B
C
D
E
1.2
A
B
C
D
E
1.3
A
B
C
D
E
1.4
A
B
C
D
E
1.5
A
B
C
D
E
1.6
A
B
C
D
E
1.7
A
B
C
D
E
1.8
A
B
C
D
E
1.9
A
B
C
D
E
1.10 A
B
C
D
E
1.11 A
B
C
D
E
1.12 A
B
C
D
E
1.13 A
B
C
D
E
1.14 A
B
C
D
E
1.15 A
B
C
D
E
1.16 A
B
C
D
E
1.17 A
B
C
D
E
1.18 A
B
C
D
E
1.19 A
B
C
D
E
1.20 A
B
C
D
E
2





