 |
DSD821S - DATABASE SECURITY AND DATA PROTECTION - 2ND OPP - JAN 2020 |
 |
1 Page 1 |
▲back to top |

NAMIBIA UNIVERSITY
OF SCIENCE AND TECHNOLOGY
FACULTY OF COMPUTING AND INFORMATICS
DEPARTMENT OF COMPUTER SCIENCE
QUALIFICATION: BACHELOR OF COMPUTER SCIENCE HONOURS (INFORMATION SECURITY)
QUALIFICATION CODE: O8BHIS
LEVEL: 8
COURSE: Database Security and Data Protection | COURSE CODE: DSD821S
DATE: JANUARY 2020
SESSION: 2
DURATION: 3 hours
MARKS: 100
SUPPLEMENTARY/SECOND OPPORTUNITY EXAMINATION QUESTION PAPER
EXAMINER(S)
MR. ISAAC NHAMU
MODERATOR:
DR. AMELIA PHILLIPS
THIS QUESTION PAPER CONSISTS OF 5 PAGES
(Excluding this front page)
INSTRUCTIONS
Answer ALL the questions.
Write clearly and neatly.
Number the answers clearly.
When answering questions you should be guided by the allocation of
marks in [ ]. Do not give too few or too many facts in your answers.
PERMISSIBLE MATERIALS
1. Non programmable Scientific Calculator.
 |
2 Page 2 |
▲back to top |

SECTION A (Multiple Choice questions — 10 marks)
1. A single-user database system automatically ensures
only one transaction is executed at a time.
serializability and durability
atomicity and isolation
serializability and isolation
atomicity and serializability
of the database, because
2. What is a rule that applies to the two-phase locking protocol?
Two transactions cannot have conflicting locks.
No unlock operation can precede a lock operation in a different transaction.
No data is affected until all locks are released.
No data is affected until the transaction is in its locked position.
3. All transactions must display
.
atomicity, consistency, and durability
durability and isolation
consistency, durability, and isolation
atomicity, durability, consistency, and isolation
4. The information stored in the
is used by the DBMS for a recovery requirement
triggered by a ROLLBACK statement, a program’s abnormal termination, or a system
failure such as a network discrepancy or a disk crash.
data dictionary
metadata
rollback manager
transaction log
5. A
is anamed collection of database access privileges that authorize a user to
connect to the database and use the database system resources.
user
role
profile
manager
1|Page
 |
3 Page 3 |
▲back to top |

6. A
is a named collection of settings that control how much of the database resource
a given user can use.
A. Role
B. Profile
C. Schema
D. Manager
7. SQL injection is an attack in which
passed to an instance of SQL Server.
A. malicious
B. redundant
C, clean
D. non malicious
code is inserted into strings that are later
8. Which statement is not true?
A. SQL injection vulnerabilities occur whenever input is used in the construction of an
B. SQL query without being adequately constrained or sanitized SQL injection allows an
attacker to access the SQL servers and execute SQL code under the privileges of the
user used to connect to the database
The use of PL-SQL opens the door to these vulnerabilities
None of the mentioned
9. Purpose of DDL Trigger is to:
Perform administrative tasks
Create tables
Regulating database operations.
AandC
10. Which of the following statement is true?
A. Views could be looked as an additional layer on the table which enables us to protect
intricate or sensitive data based upon our needs
Views are virtual tables that are compiled at run time
Creating views can improve query response time
All of the Mentioned
2|Page
 |
4 Page 4 |
▲back to top |
SECTION B
Question 1
Give one technique for validation and one for verification.
[2]
Giving examples describe the following verification, validation and testing
techniques:
[8]
i.
Informal
ii.
Formal
iii.
Static
iv.
Dynamic
Question 2
a. Besides Query Restrictions and Swapping, how can inference be controlled. Outline
two methods.
[4]
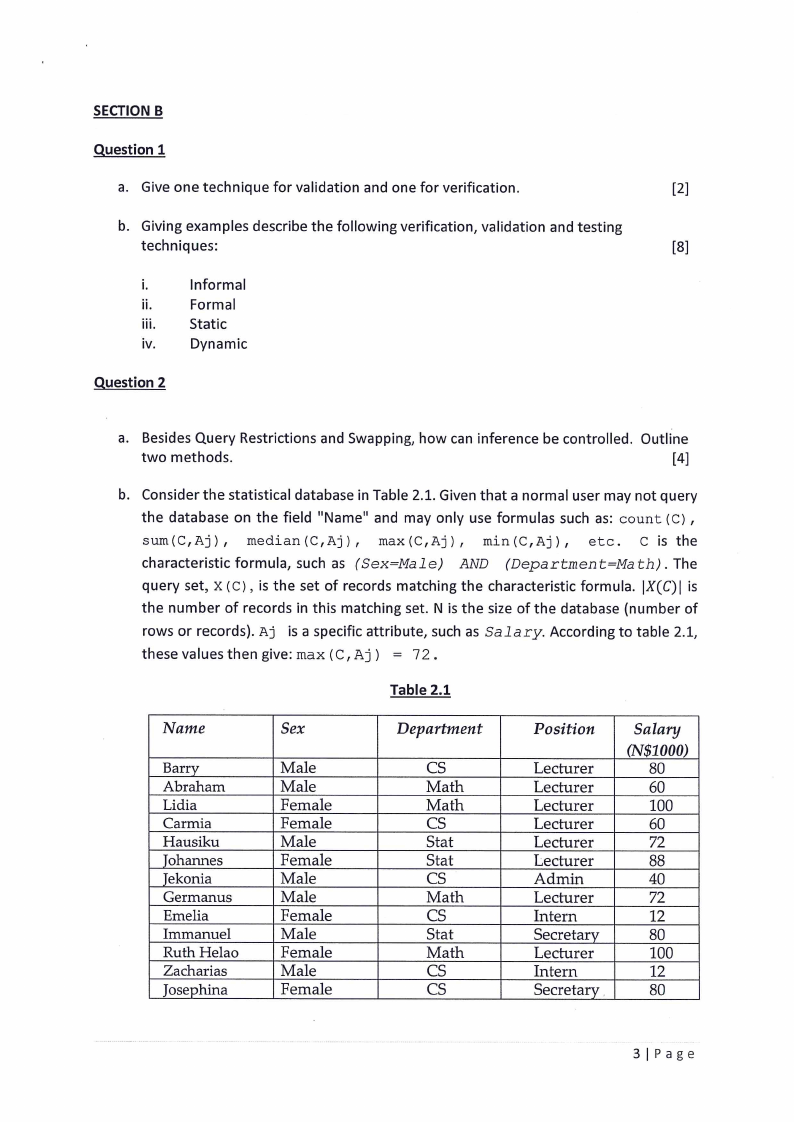
Consider the statistical database in Table 2.1. Given that a normal user may not query
the database on the field "Name" and may only use formulas such as: count (C) ,
sum(C,Aj), median(C,Aj), max(C,Aj), min(C,Aj), etc. C is the
characteristic formula, such as (Sex=Male) AND (Department=Math). The
query set, X(C), is the set of records matching the characteristic formula. |X(C)| is
the number of records in this matching set. N is the size of the database (number of
rows or records). Aj is a specific attribute, such as Salary. According to table 2.1,
these values then give: max(C,Aj) = 72.
Table 2.1
Name
Barry
Abraham
Lidia
Carmia
Hausiku
Johannes
Jekonia
Germanus
Emelia
Immanuel
Ruth Helao
Zacharias
Josephina
Sex
Male
Male
Female
Female
Male
Female
Male
Male
Female
Male
Female
Male
Female
Department
CS
Math
Math
CS
Stat
Stat
CS
Math
CS
Stat
Math
CS
Cs
Position
Lecturer
Lecturer
Lecturer
Lecturer
Lecturer
Lecturer
Admin
Lecturer
Intern
Secretary
Lecturer
Intern
Secretary
Salary
(N$1000)
80
60
100
60
72
88
40
72
12
80
100
12
80
3|Page
 |
5 Page 5 |
▲back to top |

Given that Cc isthe formula (Sex=Female) OR (Position=Lecturer) and
Aj is Salary find the values for sum(C,Aj), median(C,Aj), and
max(C,Aj).
[4]
Explain how the query size restriction technique can be used to protect the
statistical database from an inference attack. Describe it formally using N and
|X(C)| as defined above, and the constant k.
[4]
Demonstrate how the direct attack could be used to find the exact salary of
Secretary Immanuel.
[3]
iv. Give an example of how you would implement swapping on the data in table 2.1.
[2]
v. What information available to the statistical database user could be distorted by
your method in iv?
[3]
Question 3
Define at least 10 sets of standards and policies for adding, modifying and removing users
from a database.
[10]
Question 4
a. An individual may prefer to deal anonymously or pseudonymously with an
organisation for various reasons, give at least 4 reasons why this can occur.
[4]
b. With regards to personal information what do the following mean:
Implied consent
Express consent
Bundled consent
[6]
4|Page
 |
6 Page 6 |
▲back to top |

Question 5
a. Discuss, with examples, three types of problems that can occur in a multiuser
environment when concurrent access to the database is allowed.
[12]
b. The following table shows a schedule of three parallel transactions T1, T2 and T3.
Time
Ti
1
read(X)
2
X:=X-3
3
4
5
read(Z)
6
Z:=Z+1
7
write(Z)
T2
read(X)
read(Y)
X:=X+2
write(X)
T3
read(Y)
Y:=Y+1
write(Y)
read(Z)
Using diagram or otherwise, determine whether the schedule above is
serializable or not.
[8]
Question 6
a. Describe seven ways of restricting network access in an Oracle database.
[14]
b. Write a script to create a profile to be assigned to the user Ruva called SuppExam that
has the following restrictions:
[6]
Users are logged out after 15minutes of being idle.
A user who logs in 4 times with the wrong password is locked out.
A password can only be used for 90 days.
A password can only be reused 5 times.
A user is allowed 7 days to change the password after it has expired.
<<<<<<<<<<< END OF PAPER >>>>>>>>>>
5|Page





