 |
APC811S - APPLIED CRYPTOGRAPHY - 1ST OPP - JUNE 2022 |
 |
1 Page 1 |
▲back to top |

n Am I BI A u n IVER s ITY
OF SCIEn CE Ano TECH n OLOGY
FACULTY OF COMPUTING AND INFORMATICS
DEPARTMENT OF COMPUTER SCIENCE
QUALIFICATION:
BACHELOROF COMPUTERSCIENCE
QUALIFICATION CODE: 08BHIF
COURSE: APPLIED CRYPTOGRAPHY
DATE: JUNE 2022
DURATION: 2 HOURS
LEVEL: 8
COURSE CODE: APC811S
SESSION: 1
MARKS: 60
EXAMINER(S)
FIRST OPPORTUNITY EXAMINATION QUESTION PAPER
DR MERCY CHITAURO
MODERATOR:
MS ESNA MANGUNDU
THIS QUESTION PAPER CONSISTS OF 3 PAGES
(Excluding this front page)
INSTRUCTIONS
1. Answer all questions.
2. Write all your answers in the answer booklet provided and number every question.
3. Please, ensure that your writing is legible, neat and presentable.
4. Marks/scores per question are given in square brackets [ ].
5. Calculators are permitted
6. Do not use or bring into the examination venue books, mobile devices and other material
that may provide you with unfair advantage. Should you be in possession of one right now,
draw the attention of the examination officer or invigilator.
7. All things that should not be marked, e.g. any "rough work", have to be crossed out
unambiguously.
 |
2 Page 2 |
▲back to top |

1.
Cryptolocker Cryptolocker is a malware released in September 2013, Cryptolocker
spread through email attachments and encrypted the user's files so that they couldn't
access them. The hackers then sent a decryption key in return for a sum of money, usually
somewhere from a few hundred pounds up to a couple of grand (Norton.com, 2017).
a.
Which information security property is breached when a user is not able to
access files that they are authorised to view and modify?
[1]
b.
Explain why the legitimate users are not able view access their files.
[2]
c.
If the hacker gives the users, the correct decryption key will the users be able to
access their files?
[1]
d.
If your answer in 'le' is yes explain how the users will be able to access their
files. If your answer is no explain why the users will not be able to accesstheir files.
[2]
e.
Given that the users are able to accessthe encrypted files. Why would the users
still not be able to understand what is contained in their files?
[2]
f.
Suppose the users had already encrypted their files before the hackers
encrypted them. Would the users have been able to accesstheir files after they had
been encrypted by the hackers? Explain your answer.
[3]
g.
Which security property/objective would the users have achieved against the
hackers given the description in (lf).
[1]
2.
a.
Cryptography can be used to obtain security objective of authentication. Which
other security property or objective can be achieved using cryptography? Mention 2
only.
[1]
b.
Suppose emails sent from Zenane will be authenticated using message
authentication codes (MAC}. Explain in detail how Adelina will ensure integrity of
the message sent from Zenane to him using MAC.
[10]
C.
Explain how Adelina verifies that Zenane sent the email in "2b".
[4]
Pagc214
 |
3 Page 3 |
▲back to top |
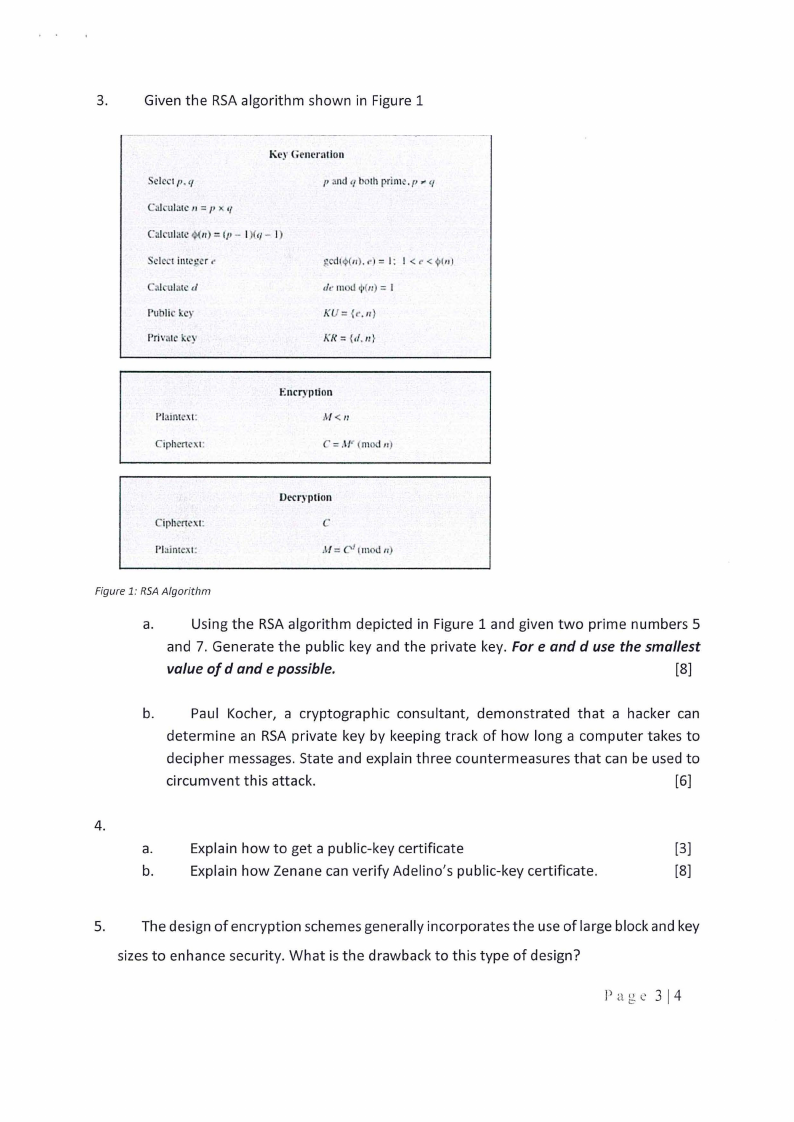
3.
Given the RSAalgorithm shown in Figure 1
---
------------
Key Gl'm:rntiou
C:il ul. te 11 = p ,,
p ncl 1/ bolh print . p,, q
Cal ula1ci.(11 =Ip- ll q-1
etc l illl •• r ,.
C~I ula1c d
Pubii kc·
:; l(¢(rr). ,· = I: I<,.
,fr mod ,(11 = I
K = {1·.11)
Kf< = {d. 11}
<!>(11)
Plaimex1:
Ciphrnexi:
Encryption
M II
C= .11'(mod 111
iph fli~xl:
Pl:!int xi:
Dt'<:ryption
Figure 1: RSAAlgorithm
a.
Using the RSAalgorithm depicted in Figure 1 and given two prime numbers 5
and 7. Generate the public key and the private key. Fore and d use the smallest
value of d and e possible.
[8]
b.
Paul Kocher, a cryptographic consultant, demonstrated that a hacker can
determine an RSA private key by keeping track of how long a computer takes to
decipher messages. State and explain three countermeasures that can be used to
circumvent this attack.
[6]
4.
a.
Explain how to get a public-key certificate
[3]
b.
Explain how Zenane can verify Adelina's public-key certificate.
[8]
5.
The design of encryption schemes generally incorporates the use of large block and key
sizes to enhance security. What is the drawback to this type of design?
Page 314
 |
4 Page 4 |
▲back to top |

a.
DESis an example of which type of encryption algorithm?
[1]
b.
DES decryption rule is as follows: Use the ciphertext as input to the DES
algorithm, but use the subkeys Kn in reverse order. That is, use K15on the first
iteration, K1son the second iteration, and so on until K1is used on the 16th and last
iteration.
i. Which key is used on the first iteration?
[1]
ii. Which key is used on the sixth iteration?
[1]
c.
Given: the hexadeximal plaintext: 0123456789ABCDEF.
i.
Convert it to binary
[2]
d.
The first step of DESenciphering plaintext isthe initial permutation {IP}given by:
58 so 42 34 26 18 10 2
60 52 44 36 28 20 12 4
62 54 46 38 30 22 14 6
64 56 48 40 32 24 16 8
57 49 41 33 25 17 9 1
59 51 43 35 27 19 11 3
61 53 45 37 29 21 13 5
63 55 47 39 31 23 15 7
What is the result of applying IP on your plaintext you got in {Sc}?
[3]
Page 414





