 |
MCF811S - MOBILE AND CLOUD FORENSICS - 1ST OPP - JUNE 2023 |
 |
1 Page 1 |
▲back to top |

nAm I BI A u n IVE RS ITV
OF SCIEnCE Ano TECHn0L0GY
FACULTY OF COMPUTING AND INFORMATICS
DEPARTMENTOF CYBERSECURITY
QUALIFICATION: BACHELOROF COMPUTERSCIENCE(HONOUR) in DIGITALFORENSICS
QUALIFICATION CODE: 08BHDS
LEVEL: 8
COURSE: MOBILE AND CLOUD FORENSICS
. ·····-·· ---
-
DATE: _JUNE2023
..
COURSECODE: MCF811S
. ..
.....
SESSION:_1(Theory)
.
-
--
DURATION: 3 Hours
MARKS: 100
--
-.
..
---
FIRSTOPPORTUNITYEXAMINATION QUESTION PAPER
EXAMINER (S)
MR. ISAACNHAM U
MODERATOR
DR. NKOSINATHIMPOFU
THIS EXAM QUESTION PAPERCONSISTSOF 5 PAGES
(Excluding this front page)
INSTRUCTIONS
1. Answer ALLthe questions on the answer scripts.
2. Write clearly and neatly.
3. Number the answers clearly.
4. When answering questions you should be guided by the allocation of marks in [ ]. Do not give too
few or too many facts in your answers.
PERMISSIBLEMATERIALS
1. None.
 |
2 Page 2 |
▲back to top |

Section A (Structured Questions}
[65 marks]
Question 1
The mobile device forensics tool classification system was created by Sam Brothers to give
investigators an overview of available tools, from least complicated to most complex, for the
purpose of gathering mobile evidence. The classification or levels are frequently illustrated as
a triangle with five layers as in Figure 1.
Chip-off
,/·
Hex Dump
Logi:caAr nalysis
Manua1 Exlraclion
Figure 1: Sam Brothers tool levelling pyramid
Explain/describe a technique used to acquire digital evidence from a mobile device at
each level, and give a scenario when each can be used.
[10]
Question 2
a. Compare digital evidence to physical evidence. In your comparison, give at least three
advantages of digital evidence over physical evidence and at least two advantages of
physical evidence over digital evidence.
[10]
a. List five digital forensics artifacts that can retrieved from a mobile phone. [5]
Page 11
 |
3 Page 3 |
▲back to top |
Question 3
a. What is cell site analysis? How is it useful to mobile forensics.
[3]
b. Expand the abbreviations, GSM and CDMA.
[1]
c. Outline two main differences that make digital forensic investigations unique for GSM
phones and CDMA phones.
[4]
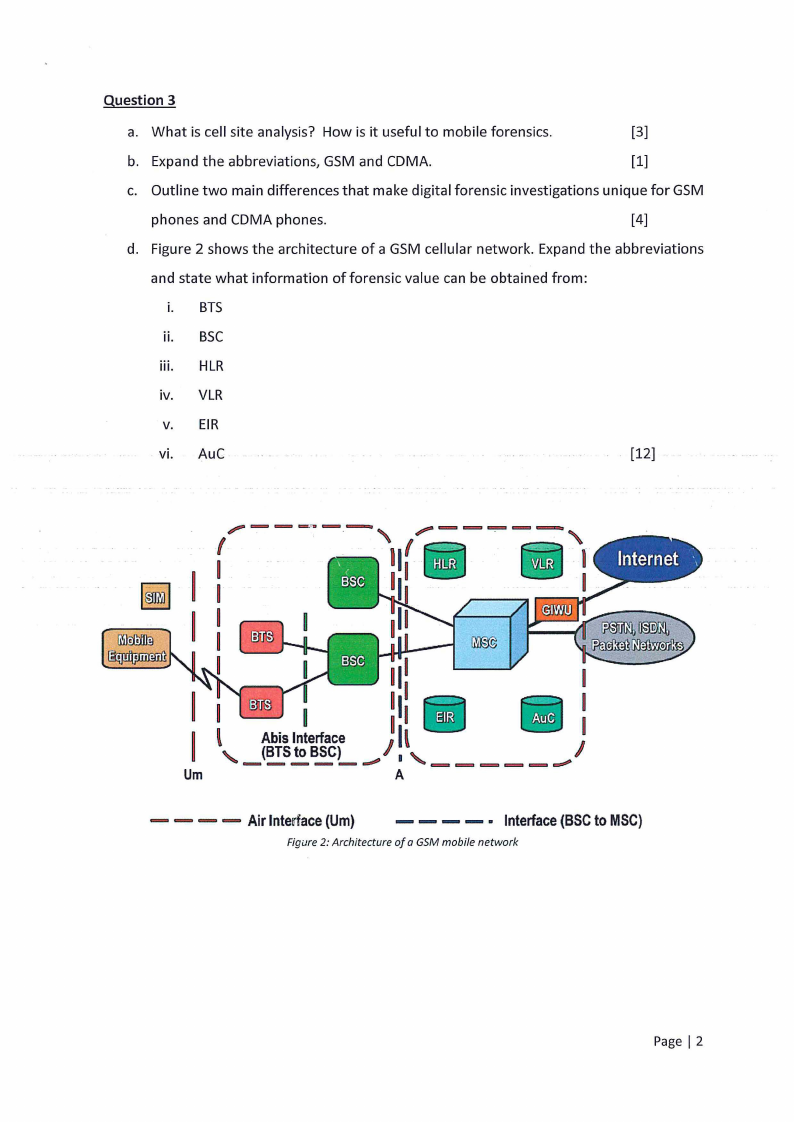
d. Figure 2 shows the architecture of a GSM cellular network. Expand the abbreviations
and state what information of forensic value can be obtained from:
i. BTS
ii. BSC
iii. HLR
iv. VLR
V. EIR
vi. AuC
[12]
Internet \\
-----Cflllllll"
- - - - AirInterface(Um) - - - - • Interface(BSCto MSC)
Figure 2: Architecture of o GSM mobile network
Page I 2
 |
4 Page 4 |
▲back to top |

Question 4
Virtualization technology makes cloud computing possible. Cloud providers set up and
maintain their own data centres. They create different virtual environments that use the
underlying hardware resources. Figure 3 below shows Type 1 and Type 2 deployment of
Hypervisors.
OS
OS
Hard,vare
Native (Bare-metal)
Hosted
Figure 3: Type 1 (left) and Type 2 (right} Hypervisors
a. Describ. e the . main difference b. etween the two?
[2]
b. - Explain in detail, two-advantages of acquiring evidenc·efrom a Type 1 over a Type·2
hypervisor system.
[4]
c. Explain in detail, two advantages of acquiring evidence from a Type 2 over a Type 1
hypervisor system.
[4]
Page I 3
 |
5 Page 5 |
▲back to top |
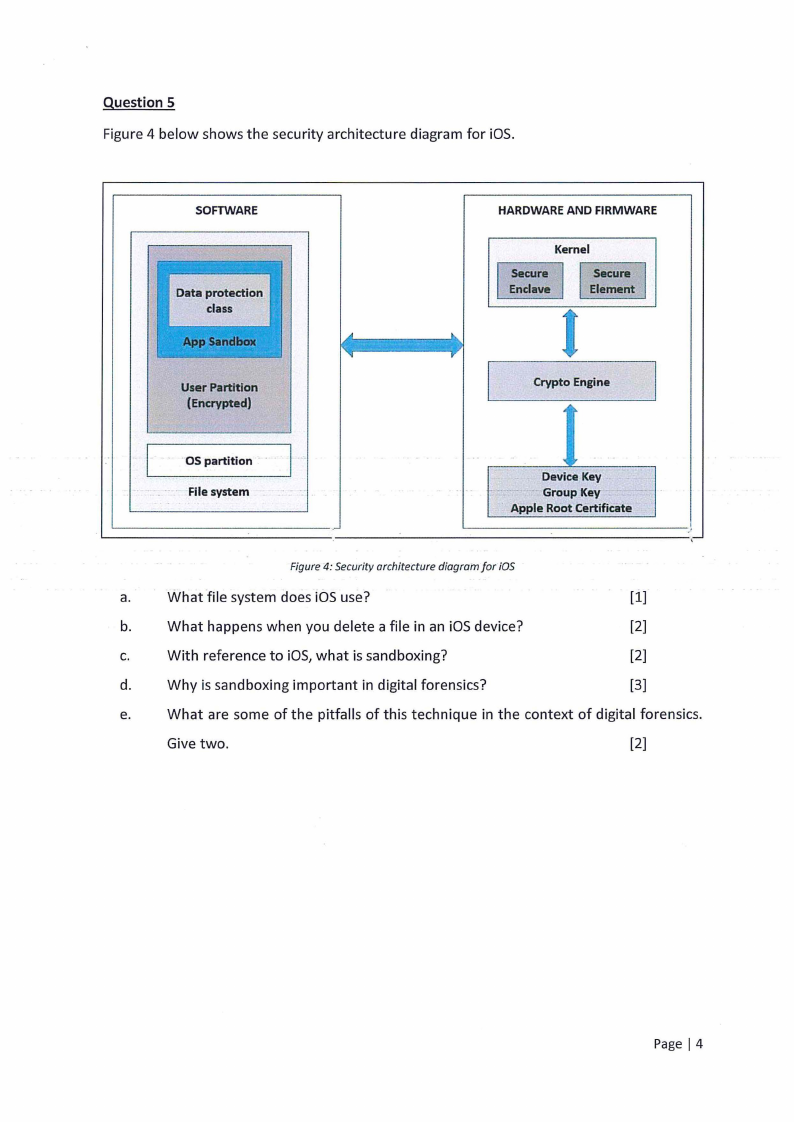
Question 5
Figure 4 below shows the security architecture diagram for iOS.
SOFTWARE
Data protection
class
HARDWARE AND FIRMWARE
Kernel
Secure
Enclave
Secure
Element
User Partition
(Encrypted)
Crypto Engine
~--·-o_s_p_a_rt_i_ti_o_n ~,---
File system
Device Key
Group Key
Apple Root Certificate
Figure 4: Security architecture diagram for iOS
a.
What ·file system does 105use?
[i]
b.
What happens when you delete a file in an iOS device?
[2]
C.
With reference to iOS, what is sand boxing?
[2]
d.
Why is sandboxing important in digital forensics?
[3]
e. What are some of the pitfalls of this technique in the context of digital forensics.
Give two.
[2]
Page I 4
 |
6 Page 6 |
▲back to top |

Section B (Scenarios and Practice)
[35 marks]
Question 7
You are given that a crime was committed and in the commission of the crime an iOS device
was recovered. Given the following different scenarios, state what action can be taken to
preserve information on the device in each case:
a. Device turned on and unlocked,
b. Device turned on and locked,
c. Device turned off and without passcode,
d. Device turned off and with passcode.
[20]
Question 8
Rev~rse Engine~ring_is i~port_ant in mobil~ for~_nsicsarid might be !he only w_ayevidence on
a phone may be accessible. However, it does affect the digital forensics investigative process.
a. Besides rooting and starting the device in recovery mode, explain three ways
passcodes in Android. phones can be circum.vented.
[6]
b. How can each of the methods you identified in a. be prevented.
[3]
c. Rooting a phone is one way of circumventing passcodes,
i. Explain three ways of rooting an Android phone.
[3]
ii. List three potential dangers of rooting a phone.
[3]
<<<<<<<<END>>>>>>>>
Page I 5





