 |
MCF811S - MOBILE AND CLOUD FORENSICS - 2ND OPP - JULY 2023 |
 |
1 Page 1 |
▲back to top |
nAmlBIA UnlVERSITY
OF SCIEnCE Ano TECHnOLOGY
FACULTY OF COMPUTING AND INFORMATICS
DEPARTMENTOF CYBERSECURITY
QUALIFICATION: BACHELOROF COMPUTERSCIENCE(HONOUR) in DIGITALFORENSICS
QUALIFICATION CODE: 08BHDS
LEVEL: 8
COURSE: MOBILE AND CLOUD FORENSICS
COURSE CODE: MCF811S
DATE: JULY2023
SESSION: 2 (Theory)
DURATION: 3 Hours
MARKS: 100
SECOND OPPORTUNITY/SUPPLEMENTARY EXAMINATION QUESTION PAPER
EXAMINER {S)
MR. ISAACNHAM U
MODERATOR
DR. NKOSINATHIMPOFU
THIS EXAM QUESTION PAPERCONSISTSOF 4 PAGES
(Excluding this front page)
INSTRUCTIONS
1. Answer ALLthe questions on the answer scripts.
2. Write clearly and neatly.
3. Number the answers clearly.
4. When answering questions you should be guided by the allocation of marks in [].Do not give too
few or too many facts in your answers.
PERMISSIBLEMATERIALS
1. None.
 |
2 Page 2 |
▲back to top |
Section A (Structured Questions)
[60 marks]
Question 1
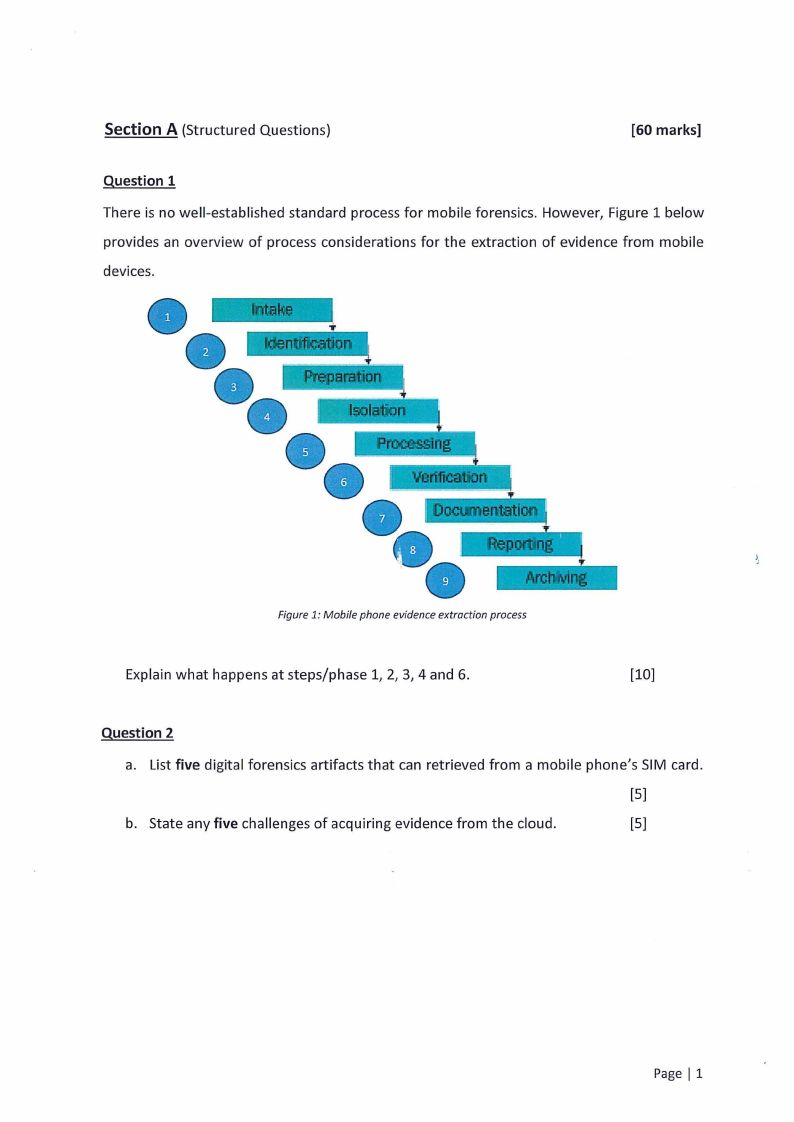
There is no well-established standard process for mobile forensics. However, Figure 1 below
provides an overview of process considerations for the extraction of evidence from mobile
devices.
'
.
.
.. ;- ,_._:_;_i~~:II/". ;
..-
Figure 1: Mobile phone evidence extraction process
Explain what happens at steps/phase 1, 2, 3, 4 and 6.
[10]
Question 2
a. List five digital forensics artifacts that can retrieved from a mobile phone's SIM card.
[5]
b. State any five challenges of acquiring evidence from the cloud.
[S]
Page 11
 |
3 Page 3 |
▲back to top |
Question 3
a. Why is it important to understand the file system of a mobile device in digital
forensics.
[2]
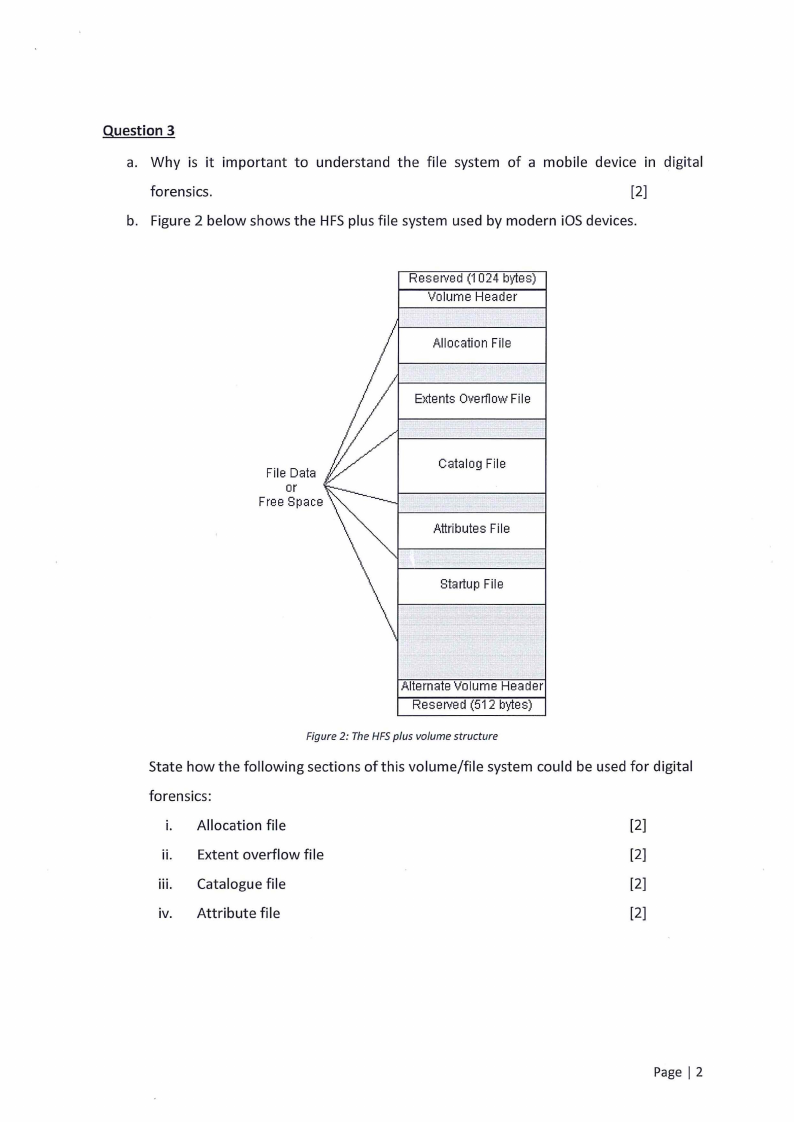
b. Figure 2 below shows the HFSplus file system used by modern iOS devices.
Reserved ("1024 bytes)
Volume Header
Allocation File
Extents Overflow File
File Data
or
Free Space
Catalog File
Attributes File
Startup File
Alternate Volume Header
Reserved (51 2 bytes)
Figure 2: The HFSplus volume structure
State how the following sections of this volume/file system could be used for digital
forensics:
i. Allocation file
[2]
ii. Extent overflow file
[2]
iii. Catalogue file
[2]
iv. Attribute file
[2]
Page I 2
 |
4 Page 4 |
▲back to top |

Question 4
Outline two benefits and three hinderance of virtualisation to cloud forensics. [10]
Question 5
Before initiating a cloud investigation, you should review the SLAto identify restrictions that
might limit the collection and analysing of data.
a. State five pieces of information that are normally included in an SLA for cloud
customers.
[5]
b. For each of the items stated in a. state how they could hinder or assist in mobile
forensics.
[5]
Question 6
Describe the following methods of accessing a passcode protected phone and outline the
risks each presents to the mobile forensics investigative process.
a. Jailbreaking
b. Rooting
[10]
Page I 3
 |
5 Page 5 |
▲back to top |

Section B (Scenarios and Practice)
[40 marks]
Question 7
The mobile industry in the world is divided between the three technologies GSM, CDMAand
iDen. It is necessary for us to understand the basic differentiation of the three technologies
as they may have an impact on the Forensic Investigative process.
i. Present the fundamental technical aspects of the three systems in your
presentation describe briefly how each affects the mobile forensics
investigative process.
[15]
ii. Describe the two main challenges of 5G technologies on the mobile forensics
investigative process.
[5]
Question 8
While searching inside the house of a person under investigation, law enforcement agents
found and seized, among other things, computers and a smartphone. After cataloguing and
documenting everything, they put all the materials into boxes to bring them back to the
laboratory. Once back in their laboratory, when acquiring the smart phone in order to proceed
with the forensics analysis, they noticed that the smartphone was empty and it appeared to
be brand new. The owner had wiped it remotely.
This therefore emphasises the importance of isolating the mobile device from all radio
networks as a fundamental step in the process of preservation of evidence:
a. There are several ways to achieve this (isolating mobile phones), all with their own
pros and cons. Outline five forensic methods of isolating mobile phone give at least
one pro and one con of ea!=h.,
[15]
b. List any other five anti-forensics techniques that are used in an attempt to affect the
mobile investigative process.
[5]
<<<<<<<<END>>>>>>>>
Page I 4





