 |
DFM811S - DIGITAL FORENSICS MANAGEMENT - 2ND OPP - JULY 2023 |
 |
1 Page 1 |
▲back to top |
nAm I BIA un IVE RSITY
OF SCIEn CE Ano TECHn
FACULTY OF COMPUTING AND INFORMATICS
DEPARTMENTOF CYBERSECURITY
QUALIFICATION: BACHELOROF COMPUTERSCIENCEHONOURS(DIGITAL FORENSICS)
QUALIFICATION CODE: 08BHDF
LEVEL: 8
COURSE: DIGITAL FORENSICSMANAGEMENT COURSE CODE: DFM811S
DATE: JULY2023
PAPER: THEORY
DURATION: 3H
MARKS: 100
SECOND OPPORTUNITY/SUPPLEMENTARY EXAMINATION QUESTION PAPER
EXAMINER(S)
MR. JULIUSSILAA
MODERATOR:
DR. AMELIA PHILLIPS
THIS QUESTION PAPER CONSISTS OF 2 PAGES
(Excluding this front page)
INSTRUCTIONS
1. Answer ALL the questions on the answer scripts.
2. Write clearly and neatly.
3. Number the answers clearly.
PERMISSIBLE MATERIALS
1. Calculator.
 |
2 Page 2 |
▲back to top |
Question 1
"Of the disciplines that encompass digital forensics is perhaps the one most closely
defined by legal requirements, and one whose growth and evolution is
informed and guided by case law, regulatory changes, and the ability of cyberlawyers
and digital forensics experts to take the products of forensic tools and processes to court"
(Ryan & Shpantzer,2002).
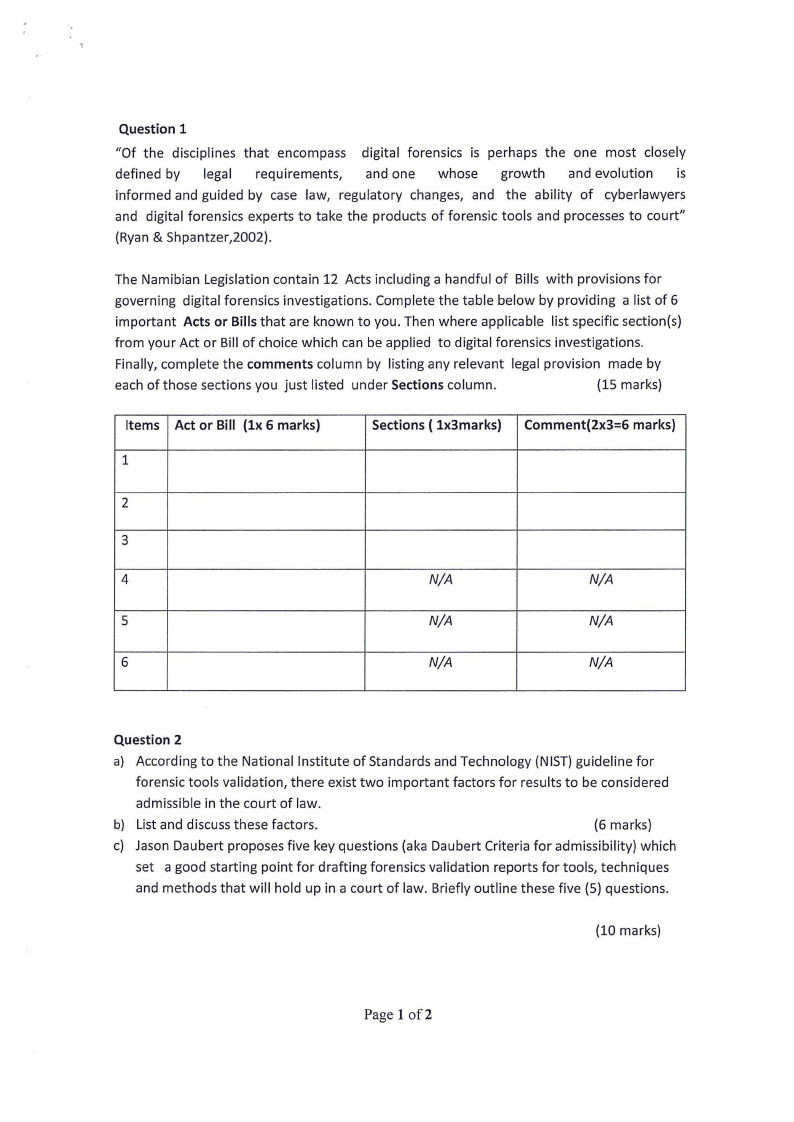
The Namibian Legislation contain 12 Acts including a handful of Bills with provisions for
governing digital forensics investigations. Complete the table below by providing a list of 6
important Acts or Bills that are known to you. Then where applicable list specific section(s)
from your Act or Bill of choice which can be applied to digital forensics investigations.
Finally, complete the comments column by listing any relevant legal provision made by
each of those sections you just listed under Sections column.
(15 marks)
Items Act or Bill (lx 6 marks)
1
Sections ( lx3marks) Comment(2x3=6 marks)
2
3
4
N/A
N/A
5
N/A
N/A
6
N/A
N/A
Question 2
a) According to the National Institute of Standards and Technology (NIST) guideline for
forensic tools validation, there exist two important factors for results to be considered
admissible in the court of law.
b) List and discuss these factors.
(6 marks)
c) Jason Daubert proposes five key questions (aka Daubert Criteria for admissibility) which
set a good starting point for drafting forensics validation reports for tools, techniques
and methods that will hold up in a court of law. Briefly outline these five (S) questions.
(10 marks)
Page 1 of2
 |
3 Page 3 |
▲back to top |

Question 3
A closer look at Network forensic investigation reveals that the procedure for collection,
preservation, documentation etc. can be very cumbersome if compared to ordinary
Computer forensics investigations. Discuss how the following can pose challenges during a
network forensics investigation.
(12 marks)
i. Search warrant
ii. Required time for evidence collection
iii. Byte by byte copy of network computer
Question 4
a)"Digital investigations can fall I into two categories: public-sector and private-sector
investigations. Although private-sector investigations often start as civil cases, they can
develop into criminal cases; likewise, a criminal case can have implications leading to a civil
case" (Nelson, Phillips & Steurt,2016).
a) Outline any five (5) most common types of litigation in private sectors.
(5 marks)
b) Discussthe most important precaution an expert should take into consideration
when conducting a digital forensics investigation for a private company.
(5 marks)
Question 5
a) Briefly describe the main objective or contribution of Sedona principles in e-discovery.
(5marks)
b) E-discovery litigations are characterized by overwhelming amount of electronic
evidence creating necessity for reducing the volume of information to what is relevant.
Describe by means of a well labelled diagram a step-by-step approach for addressing
the above-mentioned concerns.
(12 marks)
Question 6
A bank has hired your firm to investigate employee fraud. The bank uses four 20 TB
machines on a LAN. You're permitted to talk to the network administrator, who is familiar
with where the data is stored. What diplomatic strategies should you use? Which
acquisition method should you use? Write a one to two pages report outlining the problems
you expect to encounter, explaining how to rectify them, and describing your solution.
Be sure to address any customer privacy issues.
(30 marks)
*****END OF PAPER*****
Page 2 of2





