 |
SAD622S - SYSTEMS ADMINISTRATION - 2ND OPP - JAN 2024 |
 |
1 Page 1 |
▲back to top |

n Am I BI A u n IVER s ITY
OF SCIEnCE Ano TECHnOLOGY
FACULTY OF COMPUTING AND INFORMATICS
DEPARTMENT OF COMPUTER SCIENCE
QUALIFICATION: BACHELOROF COMPUTERSCIENCE
QUALIFICATIONCODE: 07BACS,07BCCS,07BCCY,07BCMS
COURSE:SYSTEMSADMINISTRATION
DATE: JANUARY2024
DURATION: 2 HOURS
LEVEL: 6
COURSECODE: SAD622S
SESSION: 2
MARKS: 50 (100%)
SECONDOPPORTUNITY/SUPPLEMENTARYEXAMINATION QUESTIONPAPER
EXAMINER(S)
MODERATOR:
MR. SHADRECKCHITAURO
MS. ALBERTINASHILONGO
MS. NDESHIHAFELAKAKWAMBI
MS. LINEEKELASHISHIVENI
MS. HELENAHAINANA
MS. TALENIANDJAMBA
MR. ISAACNHAMU
THIS QUESTIONPAPERCONSISTSOF 6 PAGES
(Excluding this front page)
INSTRUCTIONS
1. Answer all questions.
2. Write all your answers in the answer booklet provided and number every question.
3. Please, ensure that your writing is legible, neat and presentable.
4. Marks/scores per question are given in square brackets [ ].
5. Do not use or bring into the examination venue books, programmable calculators, mobile
devices and other material that may provide you with unfair advantage. Should you be in
possession of one right now, draw the attention of the examination officer or invigilator.
6. All things that should not be marked, e.g. any "rough work", have to be crossed out
unambiguously.
 |
2 Page 2 |
▲back to top |

1. True or False
[S]
{a) You can create a user without a password using the dsadd command in Windows
Server 2012/16/19 domain controller.
(b) RedHat PackageManager is the default package manager for RedHat distributions
and Debian distributions.
{c) Active directory can only be used on a standalone computer.
{d) The symbol> is used for output redirection.
{e) The NS record in DNS is found in both forward and reverse lookup zone.
2. Multiple Choice
[5]
i)
In Windows 10/8.1 64bit operating system, all Windows 32 bit applications will be
installed in
a) c:\\Program Files
b) c:\\Program Files (x86)
c) c:\\Users
d) c:\\Windows\\System32
ii)
In Windows which symbol will be used to create a hidden share
a)$
b)#
c) &
d) %
iii) In Linux users passwords are encrypted and stored in
a) /etc/users/encrypt
b) /etc/shadow
c) /etc/passwd
d) /etc/encrypt/passwd
iv) You have a DNS server named DCL DCl runs Windows Server 2012/16/19 R2. The
network ID is 192.168.1.0/24. An administrator creates several reverse lookup zones
as shown below. You need to identify which reverse lookup zone is configured
correctly. Which zone should you identify?
File Action View Help
<-~I~~ @§Ii 1mfaEl~
£ ONS
Name
..i
STATION254
168.192.in-addr.arpa
Li Forwardlookup Zones
192.168.1.in-addr.arpa
Ll ReverseLookupZones Qj'.1J.168.192.in-addr.arpa
Ll TrustPoints
Q;l192.168.in-addr.arpa
[j ConditionalForwarders
GlobalLogs
Type
Status
ActiveDirectory-IntegratedPr... Running
ActiveDirectory-IntegratedPr... Running
ActiveDirectory-IntegratedPr... Running
ActiveDirectory-IntegratedPr... Running
1
 |
3 Page 3 |
▲back to top |

a) 192.168.1.in-addr.arpa
c) 168.192.in-addr.arpa
b) 192.168.in-addr.arpa
d) 1.168.192.in-addr.arpa
v)
Your network contains an Active Directory domain named example.com. You create
an account for a temporary employee named saduser. You need to ensure that
sadusercan log on to the domain only between 07:30hrs and 17:30hrs from a client
computer named PCl. From which tab should you perform the configuration? Refer
to the screenshot below.
File Action View Help
I it:i Jt I x 1m191 I Ii. rm,-
saduser Properties
Member Of
Dial1n
Environment
Sesslons
Remote control
Remote Desktop Services Profile
COM+
General I-- A__d_dress ...,___A__ccount __,_ ___Profile _._ _Tel_e_;p_ h__ones__,.___.::O; rg_a_n_ ization__.,
saduser
Brstname:
.!:c,stname:
Di§Play name:
Qescfiption:
Offis;_e:
lsaduser
lsaduser
!nitials:
a) Address b) Environment c) General d) Account e) Profile
2
 |
4 Page 4 |
▲back to top |

3. Short Questions
(a) After typing winver command in Windows, you get the following output:
Version 22Hl (OS Build 19045.3447)
Based on this output, what do you understand by 22H1? What can you tell the user
of this machine to do so that this machine is not vulnerable in the network? [3]
(b) You have been hired by a certain company to rectify Linux login problems for John.
Every time John tries to logon he failed to login without any error message. You
check his entry in /etc/passwd file and it appears as follows:
john:x:537:100:John:/john:/bin/false
What will be your solution to the above problem?
[3]
(c) What is the primary reason for creating an organizational unit (OU)?
[1]
(d) What is a shell? Give one example of a shell in Linux.
[2]
(e) Refer to diagram below. You are trying to install Oracle Virtual Box 7.0.10 on
Windows 10 Professional machine.
Missing Dependencies
Python Core / win32api
Installingthe Orade VMVirtualBox7,0.10 Pythonbindings
requiresthe Python Core packageand the win32.apbi indings
to be installedfirst.
Whencontinuingthe installationof the Orade VMVirtualBox
7.0.10 Pythonbindingsnow, thoseneed to be set up
manuallylater. Refer to the Orade VMVirtualBox7.0.10 SDK
manualfur moreinformation.
Proceedwith installationnow?
Version7,0, 10
Yes .___No_=_]
(i) What do you understand by positive and negative dependencies? [2]
3
 |
5 Page 5 |
▲back to top |

(ii) Based on the error displayed in the diagram is it a positive or negative
dependency? Justify your answer.
[2]
(iii) Based on your answer for (ii) state the name of the software(s) which is/are
either positive or negative dependency.
[2]
4. Long Questions
(a) Analyse the three screenshots below and answer the questions which follow. The
screenshots were extracted from CentOS5 DNSserver.
jFilelocation: /etc/named.con~
options {
listen-on port 53 { 192.168.0.254; 127.0.0.1; };
listen-on-VG port 53 { ::1; };
directory
"/var/named";
dump-file
"/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
query-source port 53;
query-source-v6 port 53;
allow-query { localhost; 192.168.0.0/24; };
allow-query-cache { localhost; 192.168.0.254; }; };
view localhost_resolver {
match-clients { localhost; 192.168.0.0/24; };
match-destinations { localhost; };
recursion yes;
zone "example.com" IN {
type master;
file "reverse.example.zone";
allow-update { none; }; };
zone "0.168.192.in-addr.arpa" IN {
type master;
file "forward.example.zone ";
allow-update {none;};};
include "/etc/named.rfc1912.zones"; };
4
 |
6 Page 6 |
▲back to top |
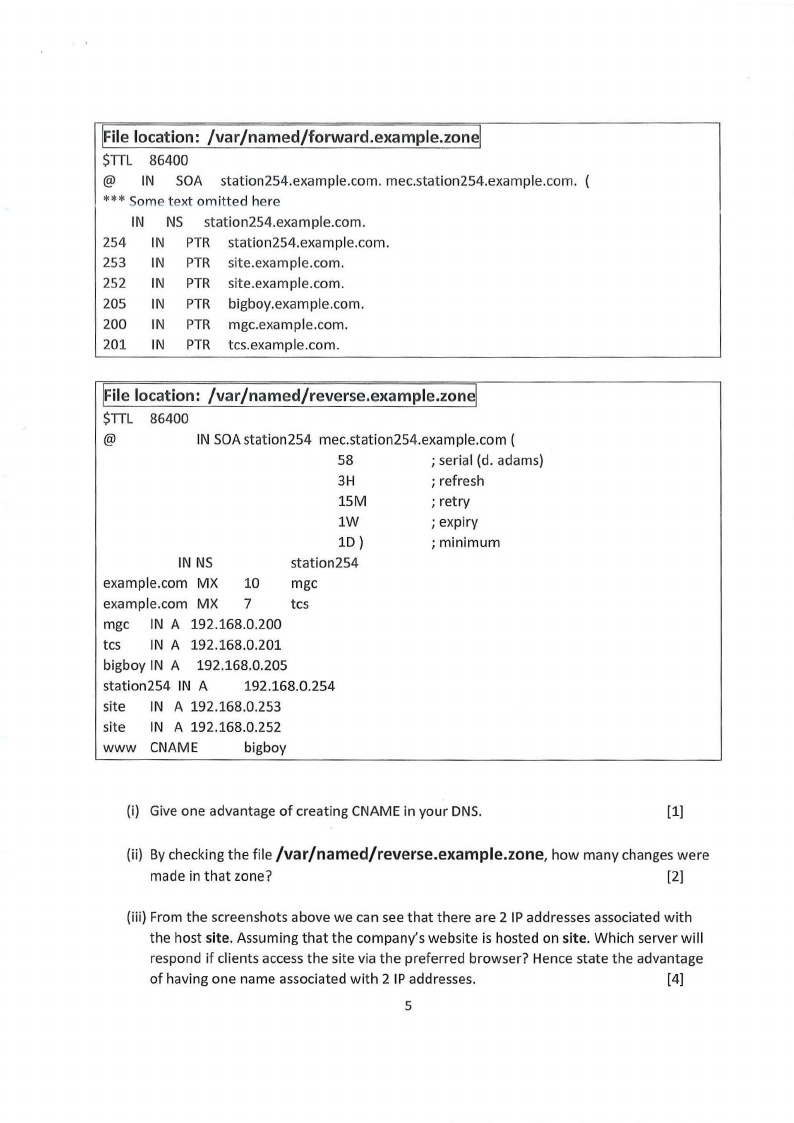
\\Filelocation: /var/ named/forward .example.zonel
$TTL 86400
@ IN SOA station254.example.com. mec.station254.example.com.
*** Some text omitted here
IN NS station254.exa m pie .com.
254 IN PTR station254.example.com.
253 IN PTR site.example.com.
252 IN PTR site.example.com.
205 IN PTR bigboy.example.com.
200 IN PTR mgc.example.com.
201 IN PTR tcs.example.com.
\\File location: /var/named/reverse.example.zone!
$TTL 86400
@
IN SOAstation254 mec.station254.example.com (
58
; serial (d. adams)
3H
; refresh
15M
; retry
lW
; expiry
1D )
; minimum
IN NS
station254
example.com MX 10 mgc
example.com MX 7
tcs
mgc IN A 192.168.0.200
tcs IN A 192.168.0.201
bigboy IN A 192.168.0.205
station254 IN A
192.168.0.254
site IN A 192.168.0.253
site IN A 192.168.0.252
WWW CNAME
bigboy
(i) Give one advantage of creating CNAME in your DNS.
(1)
(ii) By checking the file /var/named/reverse.example.zone, how many changes were
made in that zone?
[2]
(iii) From the screenshots above we can see that there are 2 IP addresses associated with
the host site. Assuming that the company's website is hosted on site. Which server will
respond if clients access the site via the preferred browser? Hence state the advantage
of having one name associated with 2 IP addresses.
(4)
5
 |
7 Page 7 |
▲back to top |

(iv) You have been hired as email server specialist to resolve email problems. Use the
screenshots above to answer these questions.
(a) which email address will be used to send DNS related errors?
[2]
(b) Which server is the preferred email server?
[1]
(c) How can you set the other server as the preferred mail server?
[2]
(v) If the client machine accesses the url: http://www.example.com or http://www, what
is the name of the machine with the resources which will be displayed?
[2]
(vi) A user typed station254.example.com on the browser, which zone will be used to
resolve this url?
[1]
(vii)
Considering the administrator installed bind-ch root application, what will be the
advantage of using this application?
[2]
5. Linux Commands/Linux
(i) Write down the command to change the system time to 17:35hrs.
[2]
(ii) Explain the following command:
touch file{l,2,3}
[2]
(iii) write down the command to change the group of the filel created in step (ii) to
group3. Assume group3 was created already.
[2]
(iv) Explain the following command. (Assume testsed is a file)
chown
road.bl
testsed
[2]
End of question paper
6





