 |
SAD622S - SYSTEMS ADMINISTRATION - 2ND OPP - JAN 2025 |
 |
1 Page 1 |
▲back to top |
nAmlBIA unlVERSITY
OF SCIEnCE Ano TECHnOLOGY
FACULTY OF COMPUTING AND INFORMATICS
DEPARTMENT OF COMPUTER SCIENCE
QUALIFICATION: BACHELOROF COMPUTERSCIENCE
QUALIFICATIONCODE: 07BAC~07BCC~07BCCi07BCMS
COURSE:SYSTEMSADMINISTRATION
DATE: JANUARY2025
DURATION: 2 HOURS
LEVEL: 6
COURSECODE: SAD622S
SESSION: 2
MARKS: 60 (100%)
SECONDOPPORTUNITY/SUPPLEMENTARYEXAMINATION QUESTIONPAPER
EXAMINER(S)
MODERATOR:
MR. SHADRECKCHITAURO
MS. ALBERTINASHILONGO
MS. ADELHEIDGEINGOS
MS. LINEEKELASHISHIVENI
MR JOSEPHRUFUMA
MS. HELENAHAINANA
MR. ISAACNHAMU
THIS QUESTIONPAPERCONSISTSOF 6 PAGES
(Excluding this front page)
INSTRUCTIONS
1. Answer all questions.
2. Write all your answers in the answer booklet provided and number every question.
3. Please, ensure that your writing is legible, neat and presentable.
4. Marks/scores per question are given in square brackets [ ].
5. Do not use or bring into the examination venue books, programmable calculators, mobile
devices and other material that may provide you with unfair advantage. Should you be in
possession of one right now, draw the attention of the examination officer or invigilator.
6. All things that should not be marked, e.g. any "rough work", have to be crossed out
unambiguously.
 |
2 Page 2 |
▲back to top |

1. True or False
(a) The password command in Linux is used to change/set user password.
(b) A DNSserver is used to translate hostnames to their IP addresses and allocate IP
addresses dynamically.
(c) Linus Torvalds is the creator and lead developer of the Linux kernel.
(d) You can create a user without a password using the dsadd command in Windows
Server 2012 domain controller.
(e) Top level domain can be a country code.
(f) The symbol » is used to append.
(g) When promoting your domain controller for the first time, the preferred DNSserver
will be setto 127.0.0.1.
(h) Type 2 hypervisors can run on top of another operating system.
(i) In Linux you can use vi or nano to edit a file.
(j) After Windows Server 2022, the next server release will be Windows Server 2025.
(k) Linux kernel is called ntldr.
(I) There are 5 root hint servers.
(m)The loopback IP address for IPv6 is represented by ::1.
2. Multiple Choice
i)
All Windows 32 bit applications will be installed in
a) c:\\Program Files
b) c:\\Program Files (x86)
c) c:\\Users
d) c:\\Windows\\System32
ii)
In Windows, which of the following will be used to create a hidden share
a) $
b) #
c) encrypt
d) hide%
iii) Which file will be used to store user details and passwords in Windows
a) SAM
b) passwd c) shadow d) User_Pass
iv) In Linux users passwords are encrypted and stored in
a) /etc/users/encrypt
b) /etc/shadow
c) /etc/passwd
d) /etc/encrypt/passwd
1
 |
3 Page 3 |
▲back to top |

v)
After typing winver command in Windows, if you get the following output:
Version 22H2 (OS Build 19044.2130)
22H2 means:
a) 22 Versions
b) 2022 second major update
c) 4 April 2019
d) 22 February
vi) Your network contains multiple subnetworks. On one of the subnetworks, you deploy
a server named Subserverl that runs Windows Server 2012 R2. You install the DNS
Server server role on Subserverl, and then you create a standard primary zone named
example.com. You need to ensure that client computers can resolve IP addresses to
hostnames. What should you do first?
a) Convert the example.com zone to an Active Directory-integrated zone
b) Create a reverse lookup zone
c) No need to configure anything. All should work as expected
d) Configure dynamic updates for example.com
e) Create a GlobalNames zone
vii) Your network contains an Active Directory domain named example.com. The domain
contains 10 computer accounts that reside in an organizational unit (OU) named PCS.
A Group Policy object {GPO) named GPO1 is linked to PCS.GPO1 is used to assign
several user rights to a user named John. In the Users container, you create a new
user named James. You need to ensure that James is assigned the same user rights as
John on all of the client computers in PCS.What should you do?
a) Modify the settings in GPO1
b) Modify the link of GPO1
c) Move James to PCS
d) Block permission inheritance in all folders under C:\\Users folder
2
 |
4 Page 4 |
▲back to top |
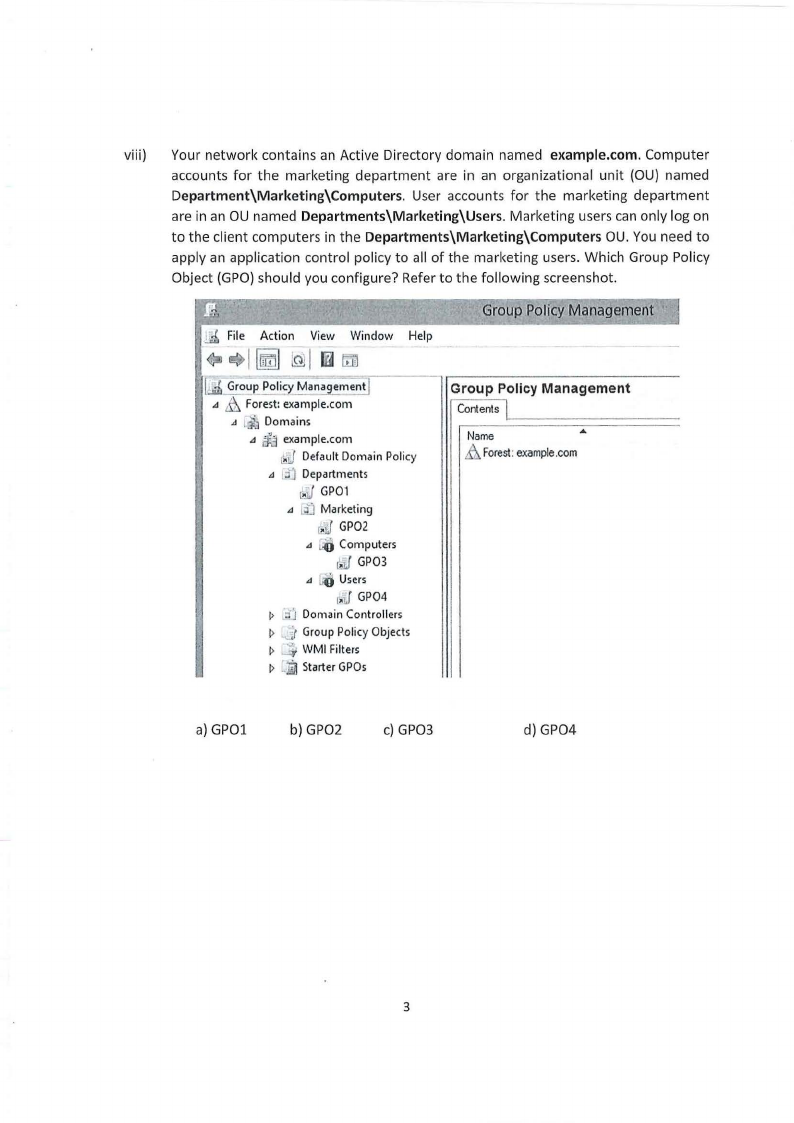
viii) Your network contains an Active Directory domain named example.com. Computer
accounts for the marketing department are in an organizational unit (OU) named
Department\\Marketing\\Computers. User accounts for the marketing department
are in an OU named Departments\\Marketing\\Users. Marketing users can only log on
to the client computers in the Departments\\Marketing\\Computers OU. You need to
apply an application control policy to all of the marketing users. Which Group Policy
Object (GPO) should you configure? Refer to the following screenshot.
_.:IiFile Action View Window Help
~~l[i]~liwu
G£Gr~~PPolicy=M=a=n=a=ge--=-m-, =e-~-,;t
£ A Forest:example.com
A ('.¥JDomains
A ff-3example.com
r•JDefaultDomain Policy
A j.'.JDepartments
1,J GP01
A Lil Marketing
~if GP02
A L=iC) omputers
~J GP03
A iiOUsers
1.J GP04
I> ;iJDomain Controllers
I> J Group Policy Objects
m I> _;;,WMIFilters
I> ... Starter GPOs
GroupPolicyManagement
Group Policy Management
Contents
----------
Name
...
£2F,.orest:example.com
a) GPOl
b)GPO2
c) GPO3
d)GPO4
3
 |
5 Page 5 |
▲back to top |

3
(a) Which term is used to refer to a malicious software which can be inserted into a
host/computer to damage or corrupt a system, replicate itself, or deny access to
networks, systems, or services?
[1]
(b) When migrating from an old system to a new system, which method is quick and
less expensive? State one disadvantage of this method.
[2]
(c) If you are a systems administrator for a company, what measures would you put in
place so that the computers within your organization are protected from computer
viruses.
[2]
(d) What is a group policy object?
[2]
(e) Explain how a systems administrator uses the ping command to test DNS
functionalities. Assume the DNS service is running on a machine with the IP:
192.168.0.200.
[2]
(f) What is a kernel?
[1]
(g) Give one reason why an administrator enables lockout policy.
[1]
(h) In Linux, you can use the Is command to display objects (files and directories) in your
current working directory. The Is -I command will list objects giving more detailed
information. Below is one line extracted from Is -I output.
- rw- - - - - - - 1 root root
d rwxr-x r-x 2 root root
- rw- r- - r- - 1 root root
- rw- r- - r- - 1 root root
drwxr-xr-x 2 will finance
[root@localhost I ~]#
1710 Oct 14 01:41 ana
4096 Nov 27 2015 Desktop
38744 Nov 27 2015 inst
0 Oct 14 02:03 sadfolder
4096 Oct 14 01:50 will
i)
How many groups are showing? Name them.
[2]
ii)
How many folders are showing? Name them.
[2]
iii) By analysing the last line from the output, explain the following section:
rwxr-xr-x
[3]
4
 |
6 Page 6 |
▲back to top |
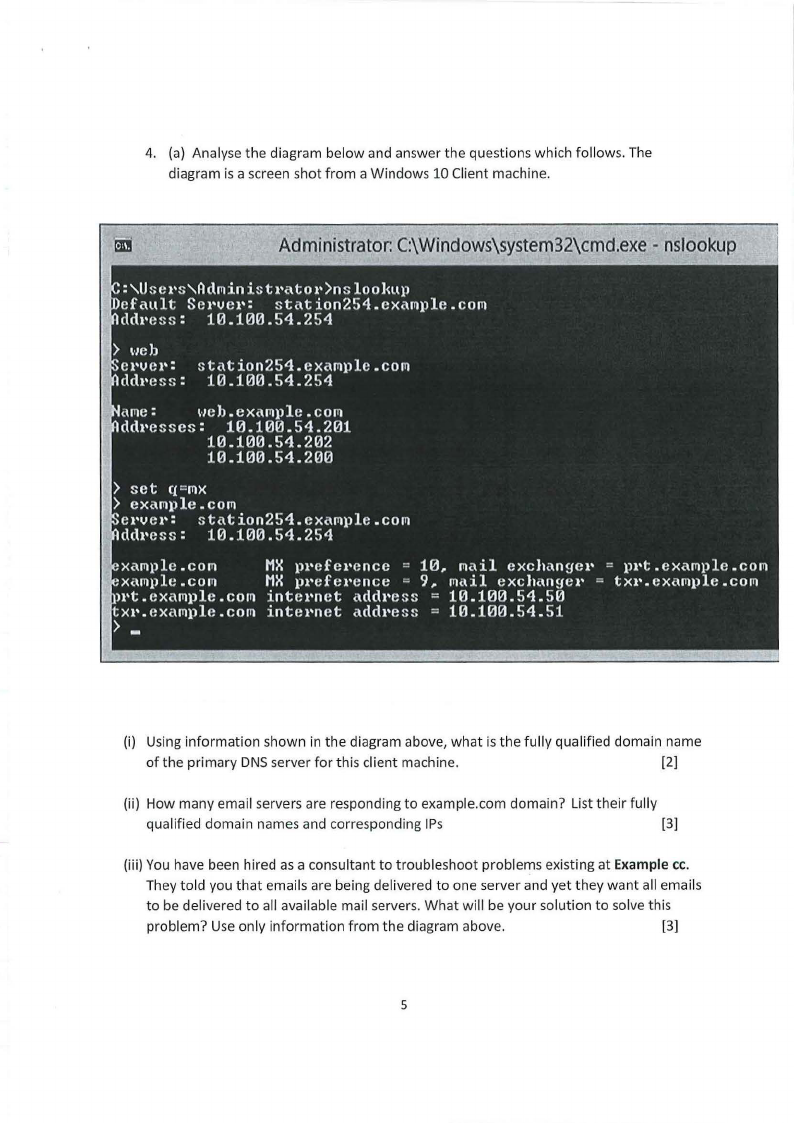
4. (a) Analyse the diagram below and answer the questions which follows. The
diagram is a screen shot from a Windows 10 Client machine.
AdministratoCr.:\\Windows\\system32\\cmd.-enxeslookup
(i) Using information shown in the diagram above, what is the fully qualified domain name
of the primary DNSserver for this client machine.
[2]
(ii) How many email servers are responding to example.com domain? List their fully
qualified domain names and corresponding IPs
[3]
(iii) You have been hired as a consultant to troubleshoot problems existing at Example cc.
They told you that emails are being delivered to one server and yet they want all emails
to be delivered to all available mail servers. What will be your solution to solve this
problem? Use only information from the diagram above.
[3]
5
 |
7 Page 7 |
▲back to top |

(iv) Assuming users can accessthe website for example cc by typing web.example.com.
which server will respond when users type web.example.com and why? [Hint: there are
3 addressesfor the same url]
[2)
(b) As an administrator you can administer active directory running a server 2012 core
edition using commands. Identify the error in the following command for adding a user
to a domain controller.
[2)
net user sad2025 P@5$wOrd /add /carcc.com
(c) Write down the result of the following command which was entered on a machine
running active directory. Remember to state the domain which was configured on the
active directory:
[3)
dsmove "cn=nust,cn=users,dc=ca,dc=eu" -newparent "ou=students,dc=ca,eu"
5. Linux Commands/Linux
(i) Write down the command to show all logged in users.
[2)
(ii) Explain the following command:
tail -20 /etc/passwd I sort > users.txt
[2)
(iii) What will be the problem of entering the following command in Linux:
[2)
useradd -g 100 tomas -p P#Nust234!7
** End of question paper**
Good Lucky
6





